Introduction
During a security assessment on FusionDirectory version 1.3 two criticalities have been identified. FusionDirectory allows to manage data archived in LDAP directories so, as you might imagine, security problems leading to an exposure of personal and enterprise could have a serious impact on the business.
Advisory
CVE-2022-36180 – Cross Site Scripting – CWE 79
| CVE-2022-36180 – Cross Site Scripting – CWE 79 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| FusionDirectory | 1.3 | 6.1 | Medium |
| OWASP CATEGORY | OWASP CONTROL | ||
| A03 – Injection | WSTG-INPV-02 WSTG-CLNT-03 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://DOMAIN/fusiondirectory/index.php?message=%5Binjection%5D https://DOMAIN/fusiondirectory/index.php?message=invalidparameter&plug=%5BInjection%5D https://DOMAIN/fusiondirectory/index.php?signout=1&message=%5Binjection%5D&plug=%5Bid%5D | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N | |||
Description
FusionDirectory does not sanitize the parameters message and plug. The value of the parameters is reflected within the HTTP response and allows a threat actor to potentially run malicious code inside the browser’s victim.
Owasp Category
A03 – Injection
Client-side scripts are used extensively by modern web applications.They perform from simple functions (such as the formatting of text) up to full manipulation of client-side data and Operating System interaction. Cross Site Scripting (XSS) allows clients to inject scripts into a request and have the server return the script to the client in the response.This occurs because the application is taking untrusted data (in this example, from the client) and reusing it without performing any validation or sanitization.If the injected script is returned immediately this is known as reflected XSS. If the injected script is stored by the server and returned to any client visiting the affected page, then this is known as persistent XSS (also stored XSS).
Proof of concept
Technical Description
The identified vulnerability is a reflected XSS, that is where, the JavaScript code that is about to be run by the unaware victim, is included in the URL itself.Thanks also to an improper cookie configuration it is possible to steal the identity of the victim that is about to visit the malicious URL, in fact triggering the code execution.
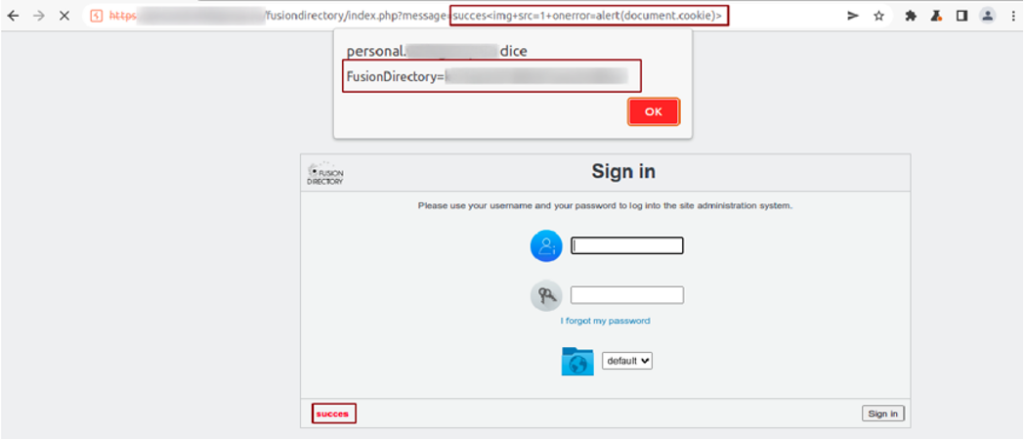
Figure 1 – Reflected XSS attack
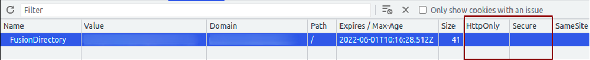
Figure 2 – Cookies not protected by the HttpOnly flags
The affected endpoints are the following:
GET /fusiondirectory/index.php?message=<img+src=1+onerror=alert(document.cookie)>
GET /fusiondirectory/index.php?message=invalidparameter&plug<img+src=1+onerror=alert(document.cookie)>
GET /fusiondirectory/index.php?signout=1&message <img+src=1+onerror=alert(document.cookie)>&plug=[id]
Impact
It must be stressed that this vulnerability can be exploited by an unauthenticated attacker, leading to an escalation of privileges in relation to the degree of the compromised user.The session cookie is not protected by the HttpOnly flag, therefore its content can be read by JavaScript and sent to the attacker machine.
Mitigation
Thanks to the close cooperation and directives given to the FusionDirectory developers, it is possible now to mitigate the previously described vulnerabilities updating the application to the version 1.3.1.
Timeline
- First contact with vendor: 28/06/2022
- Vulnerabilities confirmed by vendor: 07/07/2022
- CVE request: 12/07/2022
- Request for publication: 03/10/2022
- Agreed release date: 02/11/2022
Reference
- https://owasp.org/www-community/attacks/xss/
- https://portswigger.net/web-security/cross-site-scripting
- https://cwe.mitre.org/data/definitions/79.html
CVE-2022-36179 – Improper Session Handling – CWE 613
| CVE-2022-36179 – Improper Session Handling – CWE 613 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| FusionDirectory | 1.3 | 3.1 | Low |
| OWASP CATEGORY | OWASP CONTROL | ||
| A07 – Identification and Authentication Failures | WSTG-SESS-01 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://domain/fusiondirectory/index.php | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| AV:N/AC:H/PR:N/UI:R/S:U/C:L/I:N/A:N | |||
Description
FusionDirectory does not renew the session cookie after the user’s login process.
Owasp Category
A07 – Identifications and Authentication Failures
An improper session handling refers to an erroneous management of the session which identifies the user. Typical examples are:
- Failure to use a cryptographically strong random value as a session identifier
- Failure to protect the confidentiality of the session identification cookie
- Failure to renew the session cookie at login
- Failure to invalidate the session on logout
- Failure to automatically close the session on the server after a predefined period of inactivity.
- Failure to invalidate the session after closing the browser
Proof of concept
Technical Description
The application does not renew the session cookie after the login.More precisely, when the user visits for the first time the login page, the server assigns him a session cookie that does not change after the user uses his credentials to login.
Impact
This vulnerability elevates the impact of the previous one (XSS): it is possible to steal the session cookie and wait for the compromised user to authenticate.
Mitigation
Thanks to the close cooperation and directives given to the FusionDirectory developers, it is possible now to mitigate the previously described vulnerabilities updating the application to the version 1.3.1.
Timeline
- First contact with vendor: 28/06/2022
- Vulnerabilities confirmed by vendor: 07/07/2022
- CVE request: 12/07/2022
- Request for publication: 03/10/2022
- Agreed release date: 02/11/2022
